Information security now!
NCSC-FI has issued a severe alert on Android malware spread by SMS. The malware may steal, for example, passwords and other data from infected devices. Infected devices are also used to spread the malware further.

Malware are being spread by SMS
You receive a text message in Finnish. The message includes a link that will take you to a website asking you to download an application. The download link offers an installation package with .apk files for Android devices. The package is not an official application; instead, it contains malware. The installation files do not work on iPhones.
The website spreading the malware may also prompt you to allow the installation of applications from unknown sources. This allows unofficial applications outside app stores to be installed on your Android device. Never allow the installation of applications from unknown sources, because it will also make it possible to install malicious applications from sources other than official app stores.
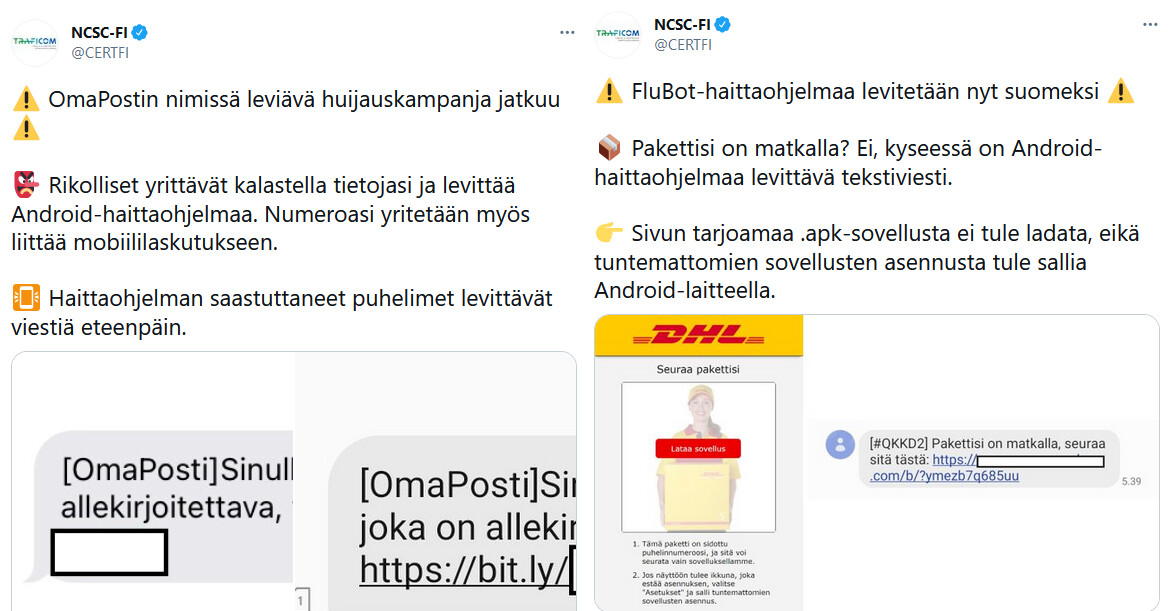
Malware may steal data from Android devices
The objectives of malware include stealing data from infected devices and using the devices to send text messages that spread the malware further. Malware can, for example, steal passwords and other data from the device. It is therefore important to protect your device by using multi-factor authentication and to reset passwords on any accounts (e.g. email and social media) used with an infected device to prevent criminals from using the data stolen by the malware.
The NCSC-FI has previously provided information about the malware FakeCop/FakeSpy targeting Android devices. This time, the malware causing trouble is called FluBot. The malware appear similar although they are based on different technical implementations. When reporting an incident to the NCSC-FI, you do not need to know which malware you are dealing with. The recommended action is the same in both cases.

IF YOU HAVE INSTALLED ANDROID MALWARE ON YOUR DEVICE:
- Perform a factory reset on the device. If you restore your settings from a backup, make sure you restore from a backup created before the malware was installed.
- If you used a banking application or handled credit card information on the infected device, contact your bank. Report any financial losses to the police.
- Reset your passwords on any services you have used with the device. The malware may have stolen your password if you have logged in after you installed the malware.
- Contact your operator, because your subscription may have been used to send text messages subject to a charge. The currently active malware for Android devices spread by sending text messages from infected devices.