Alert4/2021
The FluBot campaign has become active again, and the malware is being spread by SMS. Based on reports received by the National Cyber Security Centre (NCSC-FI), scam messages written in Finnish are being sent to tens of thousands of people in Finland.
The FluBot campaigns employs numerous different text messages with different wordings and links. The messages are written in Finnish. They are written without Scandinavian letters (å, ä and ö) and include, for example, the characters +, /, &, % and @ in illogical places in the text to make it more difficult for telecommunications operators to filter the messages. The theme of the text may be that the recipient has received a voicemail message or a message from their mobile operator. What all messages have in common is that they ask the recipient to open the link in the message. Clicking on the link does not yet install the malware. Users will be requested to allow the installation. The malware may also steal data from the device and send malware-spreading scam messages.
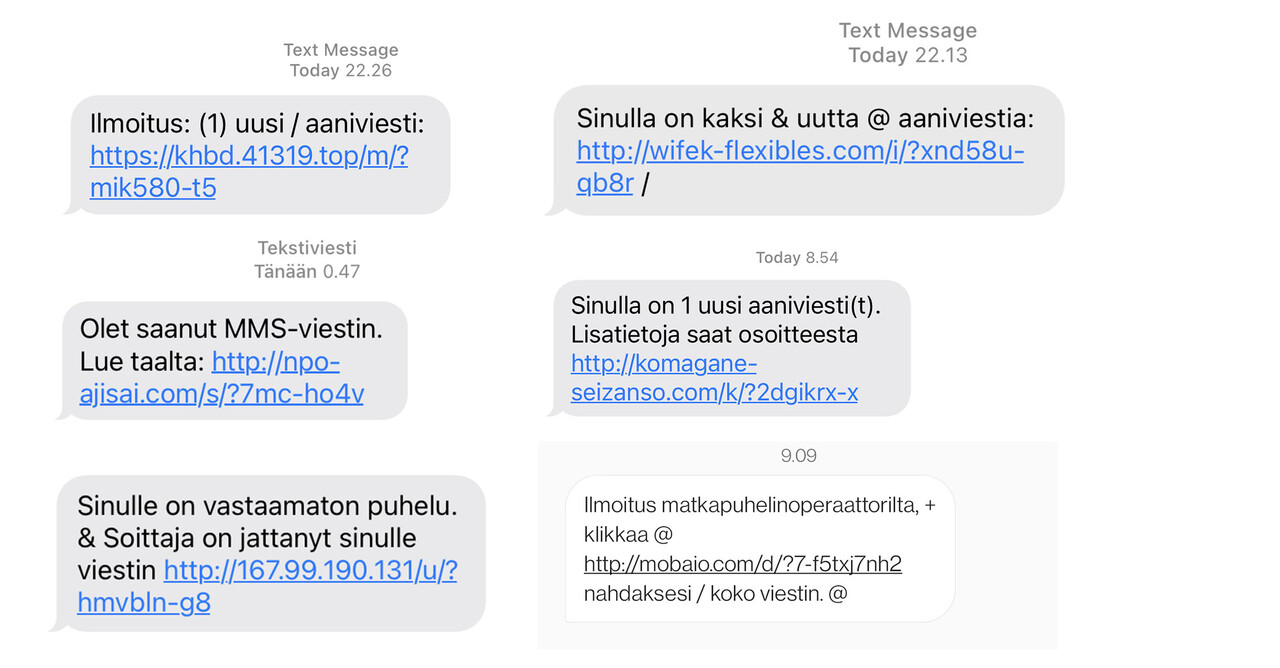
We have received many reports about FluBot messages. During previous campaigns, the malware sent messages to thousands of new victims. According to our current estimate, approximately 70,000 messages have been sent in the last 24 hours. If the current campaign is as aggressive as the one in the summer, we expect the number of messages to increase to hundreds of thousands in the coming days. There are already dozens of confirmed cases where devices have been infected.
Target group of the alert
The malware targets everyone using an Android device and a mobile subscription.
Text messages are also sent to other devices, but for example iPhone users are directed to various fraudulent sites that phish for credit card details, among other fraud attempts.
If you have received one of these messages, you have been sent a scam message and must not click on the link included. All fraudulent messages and links may lead to malware, phishing and subscription traps. We recommend that you never enter your personal data on websites if you have any doubt about the authenticity of the site.
Possible solutions and restrictive measures
Text messages written in Finnish and employing varying themes include a link to a website.
The website requests the visitor to install an application that is actually a malware.
The malware may steal data from the device and send malware-spreading scam messages. Clicking on the link does not yet install the malware. Users will be requested to allow the installation. If you have installed the malware, you need to take immediate action. The easiest way to remedy the situation is to perform a factory reset. When restoring from a backup, make sure that the backup used to restore the device was created before the malware infection. More detailed instructions can be found below.
More Information
The FluBot campaign with fraudulent messages was last active in Finland in June 2021. During the previous campaign, the messages informed the recipient about a parcel being delivered and included a link to a tracking site. The link took the user to a website that tried to get the user to install the FluBot malware. Later on, the campaign also used a voicemail theme.
NCSC-FI alert published on 4 June 2021: Android malware spread by SMS . The alert was removed on 17 August 2021.
IF YOUR DEVICE HAS BEEN INFECTED WITH FLUBOT
- Perform a factory reset on the device. If you restore your settings from a backup, make sure you restore from a backup created before the malware was installed.
- If you used a banking application or handled credit card information on the infected device, contact your bank.
- Report any financial losses to the police.
- Reset your passwords on any services you have used with the device. The malware may have stolen your password if you have logged in after you installed the malware.
- Contact your operator, because your subscription may have been used to send text messages subject to a charge. The currently active malware for Android devices spread by sending text messages from infected devices.