Information security now!
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 3–9 March 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.

Topics covered in this week’s review
- New OmaVero impersonation scam going around
- What did we learn from the Vastaamo case?
- This is how effective vulnerability coordination works
- February Cyber Weather included storm clouds caused by espionage
- This week’s vulnerabilities
New OmaVero impersonation scam going around
The NCSC-FI has been receiving reports of a new OmaVero-themed phishing campaign. On several different search engines, using the search term “OmaVero” has yielded a sponsored top search result that takes the user to a phishing site impersonating the real OmaVero website. These types of advertisements paid for by scammers can sometimes end up being offered as search results by search engines, even though service providers try to filter out malicious pages from search results.
“We submit takedown requests for phishing sites every week to take these types of malicious sites offline,” says Information Security Specialist Niclas Koskinen from the NCSC-FI.
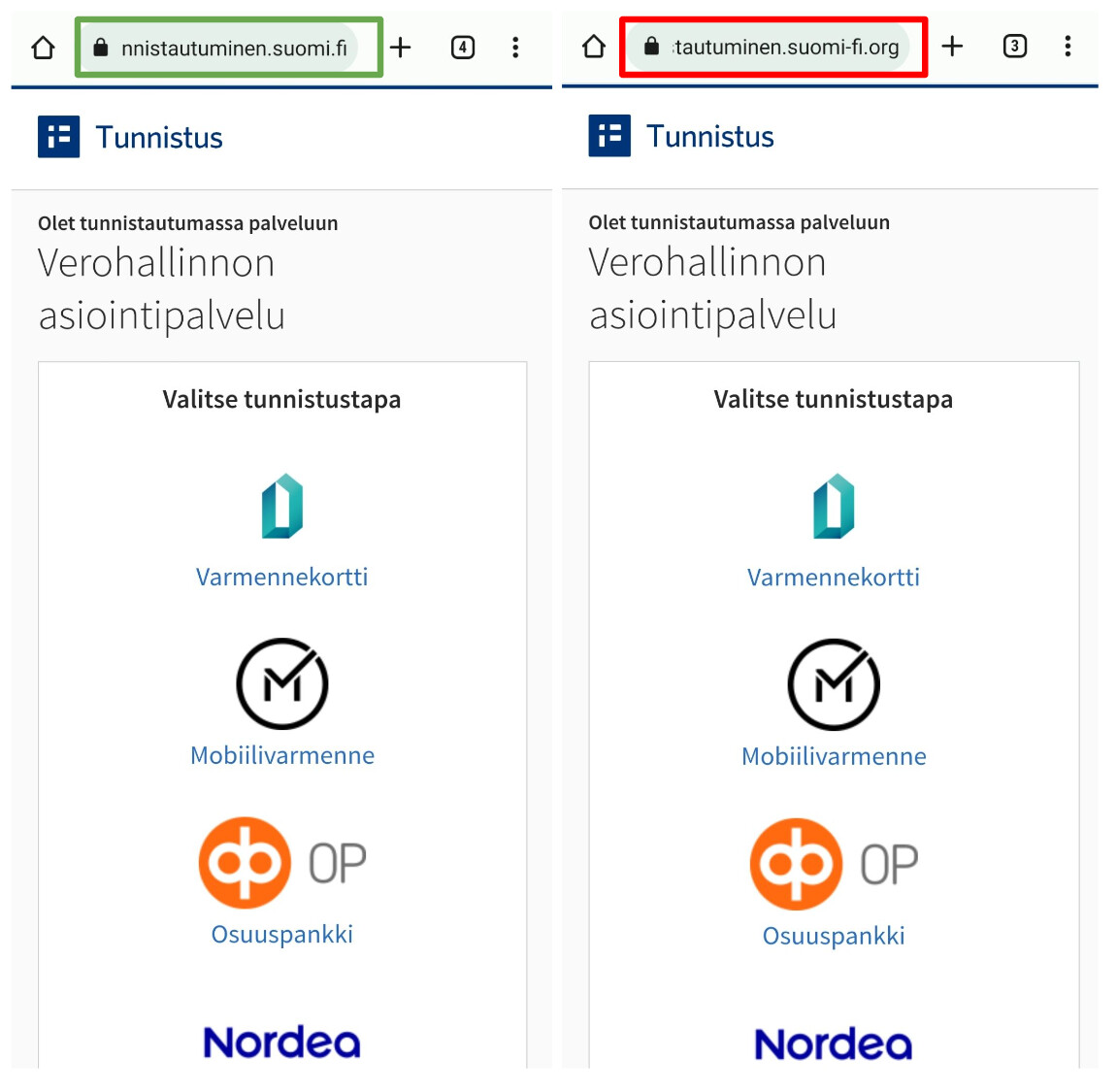
When opened on a mobile device, the malicious link takes the user to a phishing site. Users can also end up on similar phishing sites via various types of scam messages. Some of these scam messages have claimed that the user is entitled to tax returns or that they are required to pay a specific sum back to the Finnish Tax Authority.
It is a good idea to save the websites of public authorities and banks as bookmarks so that the genuine websites are always easily accessible. If you suspect that you have ended up on a malicious website, you should always check the address field of your browser, as the address is the easiest way to identify a malicious website. In this new scam, the difference in the address can be minor, such as an additional domain name ‘-fi.org’. The domain name may not be normally visible in the URL field on all mobile devices due to the length of the address.
If you have entered your information on a phishing site, immediately contact your bank and submit a police report. Acting quickly can prevent criminals from getting their hands on your account and money.
What did we learn from the Vastaamo case?
Lately, the case of psychotherapy centre Vastaamo has once again been a topic of extensive discussion in the media as a result of court proceedings and the primary suspect of the data breach being brought to Finland for questioning. The police officer in charge of the investigation, Marko Leponen, says that the police have also confiscated servers from a data centre located in Tuusula in relation to the case. The police say that they had been tracking the suspect for a long time.
The Vastaamo case teaches us that we should continue to call attention to the basics of information security. The National Bureau of Investigation’s record of the pre-trial investigation, which has been made public, includes a number of observations that all organisations could stand to learn from. Notable information security shortcomings highlighted in the record include weak passwords, administrator privilege escalation without a password and the fact that Vastaamo’s patient database was unencrypted and unanonymised. This ‘do-it-yourself’ approach to information security ultimately resulted in Vastaamo going bankrupt. The examples of invalid firewall rules show that sometimes it is a good idea to ask for outside help or have your organisation’s level of information security assessed by an external party. Many of the deficiencies noted in the record would most likely have been quickly identified in third party information security testing.
This is how effective vulnerability coordination works
Dutch information security researcher Jurjen, who lives in Finland, recently published a blog post (External link) in which he talks about information security event Disobey, a vulnerability related to the Museum Card and the vulnerability coordination carried out by the NCSC-FI.
At Disobey, Jurjen exchanged some thoughts about a vulnerability related to the Museum Card with employees of the NCSC-FI. After the event, he forwarded his findings to the NCSC-FI’s vulncoord@traficom.fi email inbox, which is monitored by NCSC-FI employees carrying out vulnerability coordination. Based on the reported findings, the NCSC-FI contacted the Museum Card organisation, and the vulnerability was quickly fixed. A big thank you to the discoverer of the vulnerability and to the Museum Card organisation!
A vulnerability means any weakness that can potentially cause damage or that can be exploited to cause damage. Vulnerabilities can be present in information systems, software, devices, processes and household automation, in addition to which they can also arise as a result of people’s actions.
There are various processes and practices in place for reporting vulnerabilities to different parties. As a general rule, vulnerabilities should not be needlessly exploited just to verify that they exist. Downloading, accessing or sharing data can meet the definition of an offence.
February Cyber Weather included storm clouds caused by espionage
The Cyber Weather in February included sunshine, rain and even some storms. Gathering storm clouds were observed when the European Union Agency for Cybersecurity (ENISA) and the CERT of the EU institutions, bodies and agencies (CERT-EU) jointly published a report to alert on sustained activity by particular threat actors. However, there was also some sunshine, particularly in the world of automation and IoT, which is also what our new instructions on the cyber security controls of industrial automation focus on.
Vulnerabilities
Fortinet released updates to address a critical vulnerability
Fortinet has released an update for its FortiOS software to fix a critical vulnerability. The vulnerability makes it possible for an attacker to execute arbitrary code on the targeted device. No methods for exploiting the vulnerability have been published, and its impacts are limited to denial of service on some FortiGate and FortiWiFi device models. If updating is not possible, the risk caused by the vulnerability can be mitigated by limiting access to the FortiOS control component until the update can be installed. The NCSC-FI published an article on the vulnerability in February 2023 (External link) (in Finnish).
CVE: CVE-2023-25610
CVSS: 9.3
Product: FortiOS & FortiProxy
Fix: Update to the latest version
Critical update for Android devices now available
Google has released its March security updates (External link) for Android. The updates fix a total of 60 issues, two of which are critical RCE (Remote Code Execution) vulnerabilities. The updates, which are being released in two parts, are for Android versions 11, 12 and 13.
The more severe of the two critical vulnerabilities enables remote code execution on a device without additional execution rights or interaction from the user of the device. In other words, it allows an attacker to execute commands without the device owner’s knowledge.
The NCSC-FI recommends that users update their Android devices without delay. Keeping your devices and applications updated is one of the best ways to maintain your personal information security.
Subscribe to the NCSC-FI’s newsletters or RSS feeds to be notified as soon as new information is published.