Information security now!
This week we talk about text messages impersonating Posti that are being used to phish for bank credentials and about how companies can improve the information security of their M365 systems.

Topics covered in this week’s review
- Dozens of reports of Posti-themed phishing text messages
- Company, here is how to protect your Microsoft 365 services
- Central government is part of society’s critical infrastructure
- Ketjutonttu helps improve the security of your supply chain
- Several critical vulnerabilities in Samsung Exynos chipsets
Dozens of reports of Posti-themed phishing text messages
The NCSC-FI has received dozens of reports of an active bank credential phishing campaign involving scammers impersonating the Finnish postal service Posti. There have also been similar phishing campaigns in the past impersonating the Finnish Tax Administration and OmaKanta. The messages do not seem to be targeted at specific recipients.
If you receive a message that appears to be from Posti, consider whether you have ordered a package that the message might be relevant to. If you have ordered a package, you can verify the authenticity of the message using ID Posti’s delivery tracking service: simply enter the item ID to check the details of the delivery. A real delivery notice from Posti will include the pick-up location of the delivery, including its address.
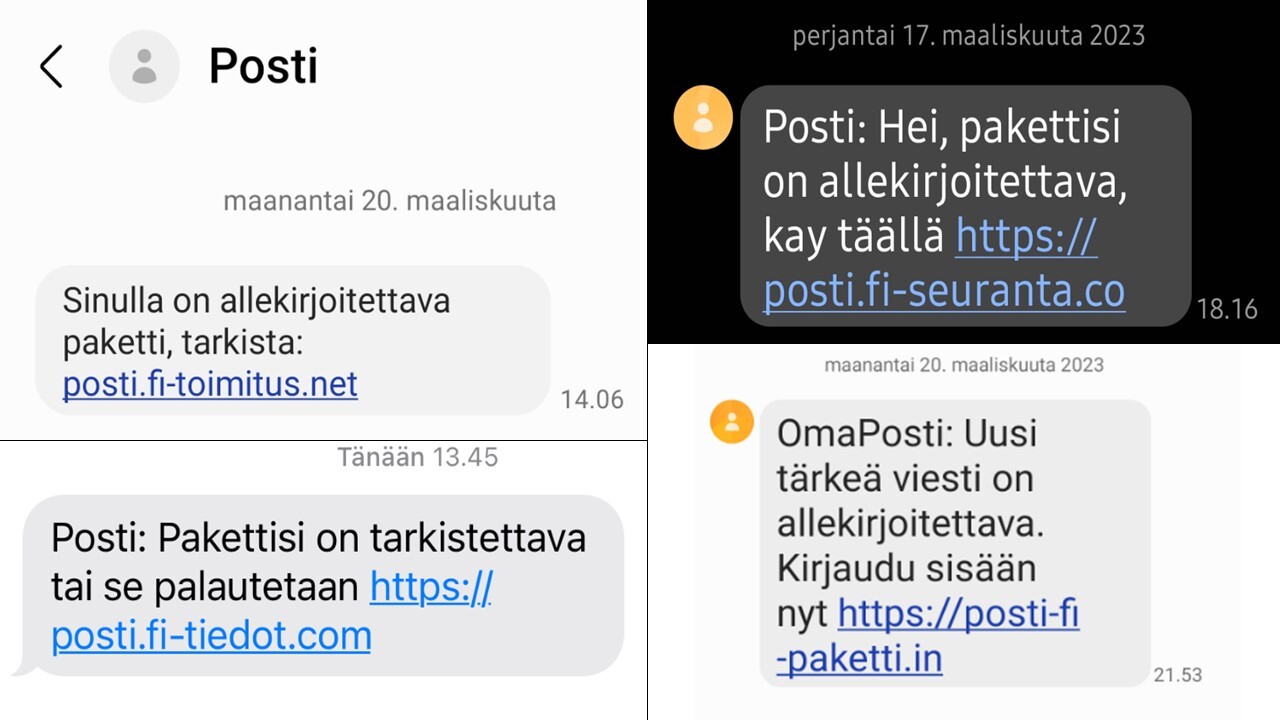
The links in the phishing messages take users to a phishing website that uses Posti’s colours and similar graphical elements as the real Posti website. Clicking the links in the text messages will eventually result in the user being asked to enter their bank credentials. Scammers also regularly phish for bank credentials in a similar manner by impersonating the largest Finnish banks. The messages and the phishing websites that their links open are written in fluent Finnish.
The sender information of the messages has been spoofed so that it seems like the messages come from the same sender as real Posti delivery notifications. Because of this, the phishing messages may be displayed in the same message chain on your mobile phone as previously received, real messages. However, being displayed in the same message chain does not guarantee that the message is genuine. This is because mobile phones have a feature that groups messages that seem to come from the same sender in the same message chain.
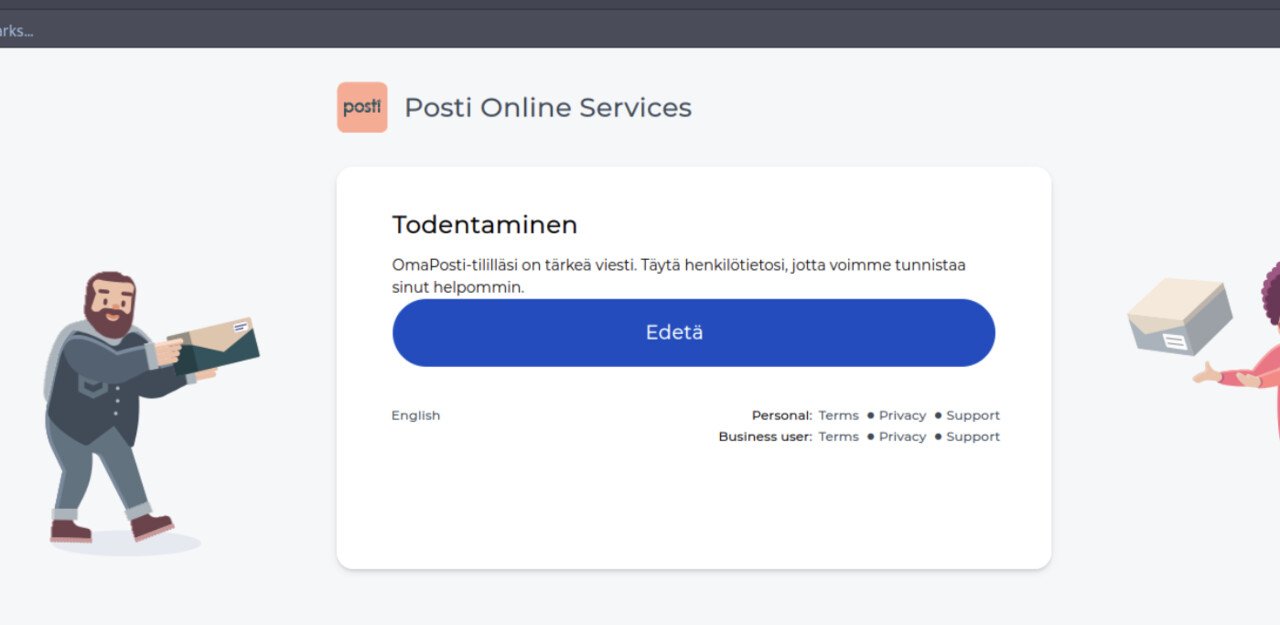
The URLs in the messages are deceptively similar to real Posti addresses. The addresses may include an additional Finnish word to make them appear more credible. There are also other Finnish-language text messages impersonating Posti going around that attempt to coerce the recipient into disclosing their information under false pretenses. We do not recommend opening any links sent via text message or entering any information on the websites that they open.
If you have entered your information on a suspicious website:
- Immediately contact your own bank.
- File a police report.
- If you wish, you can also report the incident to the NCSC-FI.
Company, here is how to protect your Microsoft 365 services
Scammers have been phishing actively for Microsoft 365 credentials during the first quarter of the year. The Microsoft 365 product was previously known as Office 365. For criminals, phishing attacks designed to steal Microsoft 365 credentials are relatively easy to carry out, especially on users who have not enabled multifactor authentication.
The NCSC-FI has received dozens of reports of Microsoft 365 phishing attacks since the start of the year.
Read our instructions: How to protect your Microsoft 365 services (in Finnish)
Go through the list and prepare a plan on how you will implement the protection measures. Some of them, such as enabling multifactor authentication (MFA), can be implemented in stages. The most important thing is to prepare and plan the changes well, while providing relevant instructions to users.
The instructions apply to Microsoft 365 Business Basic, Microsoft 365 Business Standard and Microsoft 365 Business Premium subscriptions. The changes listed do not require any additional products or licences from Microsoft.
Your company may already be using some of the protection measures. In this case, you should prepare an implementation plan for the ones that you are not using yet and also inform users of what needs to be done. Doing so will help you protect users and any data that you have stored in Microsoft 365 services.
In addition to these protection measures, it is a good idea to inform users of and provide them with training on phishing and scams. Sharing the NCSC-FI weekly reviews is an effective way of providing topical information about scams and other cyber phenomena.
Central government is part of society’s critical infrastructure
Finland is currently preparing the national implementation of the EU’s Revised Directive on Security of Network and Information Systems (NIS2), which is set to significantly expand the scope of application of the previous NIS Directive. The purpose of the NIS2 Directive is to harmonise the cyber security risk management of certain sectors critical to society and obligations related to reporting. These obligations will help ensure that companies and organisations critical to the functioning of society are able to keep up with the constantly changing cyber security operating environment. One notable change compared to the previous NIS Directive is that the NIS2 Directive will also apply to public administration.
The critical role of public administration in facilitating decision-making, good government and a functional civic society has been recognised in Finland long before the NIS2 Directive, at both the central government and local government levels. Central government with its ministries, agencies and institutes may sometimes seem abstract to citizens, but the fact is that it is a large and complex system which, in a networked and digital society like Finland, is highly dependent on online services, both in terms of safeguarding its own functioning and the information and services provided to citizens. This makes cyber security an essential factor for facilitating the functioning of central government. After all, when it comes to cyber security, ministries, agencies and government institutes face the same daily threats and challenges as other sectors and companies critical to the functioning of society: Malware, fraud attempts, denial-of-service attacks and various forms of phishing are things that central government information security experts have to deal with on a daily basis.
One effective method of easing the burden of the information security experts of ministries and agencies who strive to protect their organisations day after day is cooperation between authorities. This cooperation is facilitated by the NCSC-FI, which plays an important role in detecting various cyber threats and reporting them to various organisations. In addition to this, the NCSC-FI facilitates a number of information exchange groups between authorities and various central government organisations. This way we can all learn from one another and better understand the trends, threats and legislative changes affecting different administrative branches, for example. The creation and development of these types of confidential networks requires the commitment and contribution of all the parties involved, but for a small country like Finland, the benefits can be significant. At the same time, obstacles to information exchange are dismantled through various legislative projects in areas where they still exist.
One concrete example of cooperation between authorities across administrative branches is the protection of Finland’s upcoming parliamentary elections against cyber threats. The party responsible for organising the elections and maintaining the election information system is the Ministry of Justice together with the Legal Register Centre. The voting register and the polling station service are maintained by the Digital and Population Data Services Agency operating under the Ministry of Finance. Another party operating under the same administrative branch is Government ICT Centre Valtori, which is a notable ICT service provider for many election authorities. Many other authorities also provide surveillance or situational picture information. This information exchange between different parties is coordinated by Traficom’s NCSC-FI, which operates under the Ministry of Transport and Communications, to ensure that all election officials have access to the same situational picture and reliable connections to one another. While they may seem mundane, these efforts make a big difference in helping different administrative branches engage in cooperation to create a more cyber secure society.
Ketjutonttu helps improve the security of your supply chain
The Ketjutonttu campaign, which is part of the NCSC-FI’s Tonttu projects focusing on the feasibility testing of new methods, helps Finnish companies and their suppliers manage cyber risks in their supply chains. The campaign provides the suppliers of participating organisations with a free-of-charge information security check based on open data sources. In addition to this, suppliers are provided with assistance for implementing fixes.
Safeguarding supply chains is an important part of comprehensive security, as the trust that organisations have in their suppliers can be exploited for supply chain attacks. These types of attacks can target the partners, service providers, software or devices of organisations.
The aim of the Ketjutonttu campaign is to provide quick help to as many companies as possible. By adopting an approach based on open data sources, the campaign makes it possible to carry out information security checks on large numbers of suppliers without the need for separate agreements. Suppliers whose information security is found to be lacking based on the check are also provided with further assistance. The suppliers who have already undergone information security checks as part of the campaign have reacted positively to the results and the provided assistance, and as a result the cyber security of supply chains has been improved in a concrete manner.
The service is provided by the Finnish company Badrap Oy, which boasts years of experience regarding effective information security measures and campaigns and helping companies address information security issues.
Read more about Ketjutonttu on Badrap’s website (in Finnish) (External link)
Read more about Tonttu projects (in Finnish)
Several critical vulnerabilities in Samsung Exynos chipsets
CVE: CVE-2023-26072, CVE-2023-26073, CVE-2023-26074, CVE-2023-26075, CVE-2023-26076
CVSS: 9.8 (NIST: NVD) and 7.6 (CNA: MITRE)
What: Exploiting the vulnerability makes it possible to remotely execute arbitrary commands on the target device. The attacker only needs to know the victim’s phone number to exploit the vulnerability.
Product: Samsung Exynos chipset
Fix: The information security updates for March include fixes to the first four vulnerabilities, and the upcoming information security updates for April include a fix to the fifth vulnerability. Limiting the vulnerabilities requires action on the part of the device owner. The exploitation of the vulnerabilities can be limited by disabling Wi-Fi calls and VoLTE (Voice-over-LTE) in the device settings.
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 17–23 March 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.