Information security now!
This week we talk about an active secure email phishing campaign and the rise of the cyber threat level in Europe.

Topics covered in this week’s review
- Beware of secure email phishing messages
- Invoice fraud on the rise again
- Polish authorities report on the espionage campaign of a cyber threat actor
- The NCSC-UK reports on a heightened threat level
- The deployment of digital services and devices should be controlled
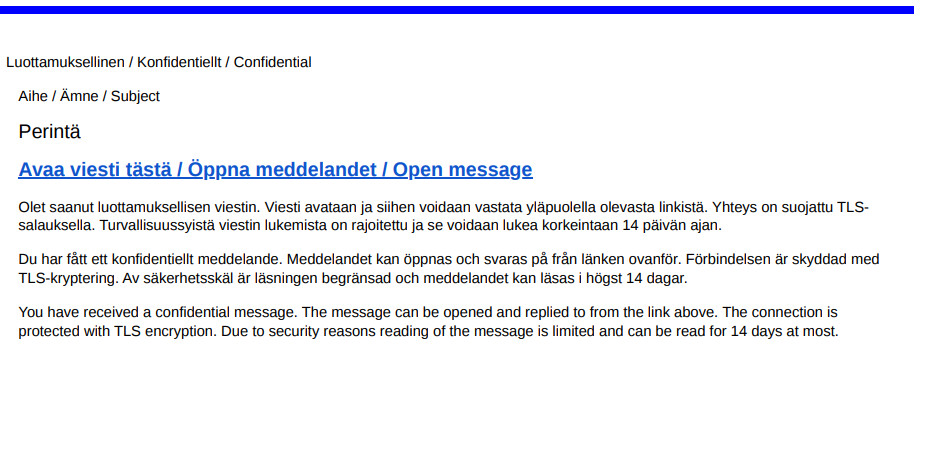
Beware of secure email phishing messages
There have been large numbers of secure email-themed phishing messages going around in recent weeks. The NCSC-FI has also received numerous reports of compromised email accounts in relation to secure email phishing. The subject lines of the emails mention ‘lasku’ (‘invoice’) or ‘hakija’ (‘applicant’), for example, and the actual message is a seemingly real-looking secure email, complete with links. Based on the reports, thousands of such messages have been sent out in recent weeks to the contact details of compromised email accounts.
“Several organisations have already fallen victim to the most recent secure email phishing campaign. The phishers have sharpened their hooks with the help of genuine-looking message templates and organisation logos,” says Information Security Specialist Olli Hönö from the NCSC-FI.
If the user enters their information on a phishing site and their account is subsequently compromised, the criminal will change the secure email message template. In several cases, the logo of the organisation whose account was compromised has been added to the new phishing messages sent out under the organisation’s name.
The NCSC-FI investigates received reports and the links included in them. When necessary, we also issue takedown notices to harmful sites and contact the organisation whose compromised email account has been used to forward phishing messages. The importance of openness cannot be overstated – if an email account is compromised, this should be immediately communicated to the rest of the organisation and to the contacts of the compromised account. If necessary, the incident can also be reported on the organisation’s website.
Any detected digital scams and phishing attempts should be reported to the NCSC-FI. By submitting a report, you can contribute to national situational awareness and help other organisations. The takedown notices issued by the NCSC-FI to harmful websites effectively cut the lines of a phishing campaign, in addition to which the NCSC-FI will contact any compromised organisations to determine whether they have noticed the incident and need any help.
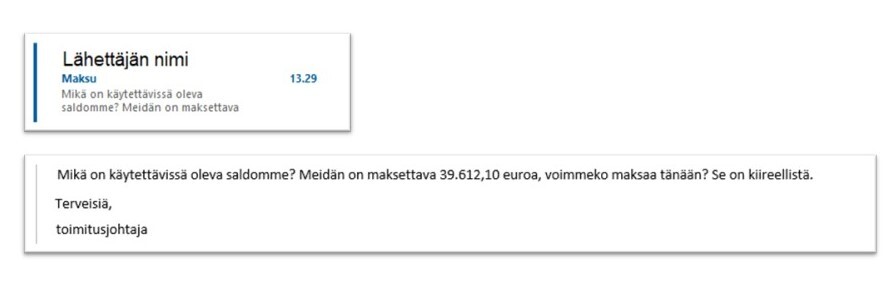
Invoice fraud on the rise again
Over the past week, the NCSC-FI has received several reports of attempted invoice fraud from different parts of Finland. All organisations should be on the lookout for such attempts and train their staff on how to deal with invoice fraud.
Invoice fraud attempts are often targeted at employees in charge of invoicing and monetary transactions at organisations. The criminal will reach out via email, claiming to be the company’s CEO or a representative of a cooperation partner, for example. After establishing contact, they will ask the recipient to make a transaction or payment. The scammer will claim that the matter is urgent and may instruct the recipient to bypass normal processes because they are in a meeting, for example. The email may come from a compromised email account or an account that has been spoofed to look like the email account of another person.
Organisations can protect themselves against invoice fraud by keeping their staff informed. It is important to establish clear practices and processes on how to handle invoices and verify their authenticity. To prevent exceptions, employees should be advised to view any sudden payment requests with suspicion.
Polish authorities report on the espionage campaign of a cyber threat actor
The Polish Military Counterintelligence Service (SKW) and CERT.PL have published a report on a widespread espionage campaign linked to cyber threat actor APT29. According to the report, the campaign aimed at collecting information from foreign ministries and diplomatic entities using targeted email phishing, i.e. spear phishing. Most of the identified targets of the campaign are located in NATO member states, the European Union and, to a lesser extent, in Africa.
The campaign described in the report attempts to spread malware using a link or attachment delivered via email that directs the user to a malware download site. The malware downloaded from the site is packaged in an ISO or IMG disk image file, for example. The malware is activated when the file is opened.
Using disk image files to spread malware is a way to bypass the ‘mark-of-the-web’ warning applied to files that tells the user that the file was downloaded from the internet. The report recommends preventing or restricting the use of disk image files on workstations.
Heightened threat of state-aligned groups against western critical national infrastructure
The National Cyber Security Centre of the United Kingdom (NCSC-UK) has issued an alert on the heightened threat of state-aligned groups against western critical national infrastructure. The alert talks of the emergence of a new class of threat actors that differ from previous ones in that they can align to Russia’s perceived interests, but are often not subject to formal state control. As a result, their actions are less constrained and their targeting broader than traditional cyber crime actors, making them less predictable.
The alert also says that while the cyber activity of these groups often focuses on DDoS attacks, website defacements and the spread of misinformation, some have stated a desire to achieve a more disruptive and destructive impact against western critical national infrastructure.
The NCSC-UK considers it unlikely that these groups have the capability to deliberately cause a destructive impact in the short term without external assistance. However, they may become more effective over time, and so the NCSC-UK is recommending that organisations act now to manage the risk against successful future attacks.
The deployment of digital services and devices should be controlled
Every now and then, the NCSC-FI receives reports of various digital services and devices being extensively and aggressively marketed to the employees of organisations. These products are very often cloud-based or easy to deploy without the support of the organisation’s own IT department. While no actual malicious activity has been uncovered based on the investigation of these types of reports so far, the NCSC-FI would like to remind everyone about the importance of risk management when it comes to deploying new services and devices.
Every device or service connected to an organisation’s data network or service environment (such as its centralised user and access management) also increases the organisation’s cyber risks. Because of this, the management staff of organisations should ensure that there are sufficient controls in place for managing these risks.
Organisations should ensure that
- all digital products and services are deployed according to a pre-defined process, taking into account the organisation’s own information security principles and requirements.
- the aforementioned principles are communicated to the organisation’s staff so that employees know to forward e.g. any marketing correspondence to the parties in charge of procurements.
- the cyber security level of the supplier of each product or service is also assessed. Is the supplier able to provide a clear explanation of how they take care of information security?
Vulnerabilities
CVE: CVE-2023-2033
CVSS: 8.8
What: Google fixed an actively exploited zero-day vulnerability in the Chrome browser.
Product: Google Chrome browser
Fix: Update Chrome to version 112.0.5615.121
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 13 April–20 April 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.