Information security now!
Email users are being plagued by active phishing. Stay vigilant! Your alarm bells should start ringing if a secure email link opens a page that asks for your username and password.

Topics covered in this week’s review
- Spoofed secure email phishing messages circulating again
- Hotel reservation service used for phishing
- Critical vulnerability in Juniper network devices
Spoofed secure email phishing messages circulating again
The spoofed secure email messages contain links that lead to a phishing site asking for your username and password. The scam messages are currently spreading between organisations in the municipal sector. If you make the mistake of clicking the link in the scam message and entering your email username and password on the website that opens up, your email account will be hijacked by criminals, who will use it for fraud and to send out more phishing messages.
The spoofed messages may have used various, believable subject lines, such as "Vuokrarästi” (“Rent overdue”) or "Arkistomateriaalitilaus” (“Archive material order”), adding to their credibility. However, your alarm bells should start ringing if a link included in a secure email message opens a page that asks for your username and password.
One effective way of protecting against phishing campaigns is to make two-factor authentication mandatory for your organisation’s users. Leaving the use of two-factor authentication up to the user does not provide the same level of protection.
The NCSC-FI last warned about secure email phishing back in April. Read more:
Email accounts compromised in a secure email phishing campaign (External link)
Hotel reservation service used for phishing
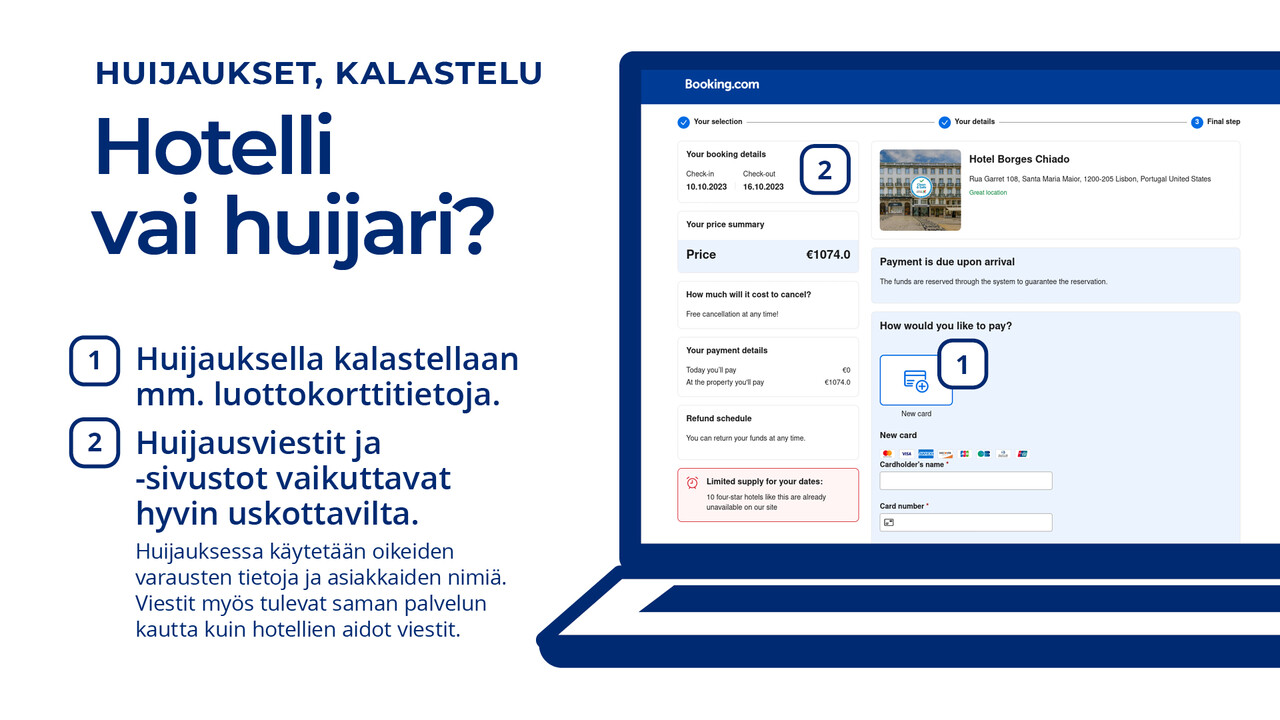
Customers of the hotel reservation service Booking.com, which is also popular among Finnish people, have reported several cases of receiving messages from the service that claimed to be from hotels, but were actually sent by scammers. The scam messages have been used to phish for credit card numbers, among other things.
The Booking.com scam messages were reported on by Ars Technica back in February 2023. The NCSC-FI has also received reports of the scam messages from Finnish customers. These reports have remained sporadic in the past, but several cases have now been reported in August.
The scam messages appear very believable, as they include real hotel information and customer names and refer to genuine hotel reservations made by customers. The messages also appear to have been sent by the real Booking.com service, just like genuine messages sent by hotels. The links included in the messages lead to spoofed websites that appear deceptively similar to a hotel’s or the reservation service’s genuine websites. Any credit card information entered on these spoofed websites ends up in the hands of criminals.
While similar cases have been reported from time to time for years, Booking.com has not confirmed to have suffered a data leak or breach. It seems possible that a criminal actor has had access to some hotel reservation data in the system, but that no credit card data has been leaked to criminals. Because of this, criminals are attempting to use the obtained data to phish for credit card numbers.
Additional information:
Critical vulnerability in Juniper network devices
CVE: CVE-2023-36844, CVE-2023-36845, CVE-2023-36846, CVE-2023-36847
CVSS: 9.8
What: Four separate minor vulnerabilities have been discovered in the operating systems of Juniper’s SRX series firewalls and EX series switches. Although these vulnerabilities appear relatively harmless by themselves, chaining them together makes it possible to bypass authentication and execute arbitrary code on affected devices. As such, combined they present a critical vulnerability that requires immediate patching.
Product: Juniper SRX firewalls, Juniper EX switches
Fix: Operating system patch
For more information (in Finnish), please visit https://www.kyberturvallisuuskeskus.fi/fi/haavoittuvuus_14/2023 (External link)
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 18–24 August 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.