Information security now!
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 7–13 October 2022). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.

Topics covered in this week’s review
- Ask us about ransomware!
- The Digital and Population Data Services Agency’s Digital Security Week
- New version of Kybermittari published – register for presentations and training events
- Material and tools published by CISA
- Police impersonation scams on the rise
- Zalando customer accounts being hijacked and exploited
- This week’s notable vulnerabilities
Ask us about ransomware!
The risk of falling victim to ransomware has increased significantly in recent years. Criminals are targeting all kinds of companies and organisations with ransomware attacks, regardless of industry or size. The topic is on a lot of people’s minds and rightly so, as preparing for threats is always worthwhile.
In recognition of the European Cybersecurity Month, we are giving the representatives of companies and organisations an opportunity to ask our experts about ransomware. For more information and a link to the question form, please see the Information Security Now! article below.
Digital security is about action!
The Digital and Population Data Services Agency’s Digital Security Week has offered fresh and insightful discussion with Finland’s leading experts throughout the week 10–14 October 2022. The daily webinars provided practical tips for understanding, managing and promoting digital security matters. The entire week’s programme has been open and free-of-charge for everyone.
If you did not catch the webinars live, you can watch recordings of them on the Digital Security Week website (External link). Simply scroll down on the website to find the recordings in chronological order. The recordings will be subtitled as soon as possible. (Website available only in FInnish and Swedish)
New version of Kybermittari published – register for presentations and training events
Kybermittari (Cybermeter) is a model that organisations can use to assess and develop the maturity of their own cyber security capabilities in order to integrate cyber security into their internal processes. In addition to functional technologies, maintaining a good level of cyber security requires the organisation’s entire personnel to be familiar with and commit to good information security practices.
The purpose of Kybermittari is to help organisations assess and develop their ability to tackle cyber threats and to facilitate cooperation and information sharing between companies. If you carry out an assessment using Kybermittari, please share the numerical results with the NCSC-FI so that they can also contribute to the national situational picture. The NCSC-FI also uses the results to generate benchmarking data for the users of Kybermittari.
If you have used the first version of Kybermittari in the past, you can migrate the numerical results over using the new Excel file. There are also separate instructions available for migrating comments.
The United States Cybersecurity and Infrastructure Security Agency (CISA) maintains a free catalogue of cyber security tools
The United States Cybersecurity and Infrastructure Security Agency (CISA) maintains a catalogue of useful and free cyber security tools on its website. The catalogue includes tools provided by CISA itself, open source tools and tools from both public and private organisations and associations. The catalogue is intended to help organisations of all sizes reduce their cyber security risks.
CISA recommends that all organisations take measures to improve their level of cyber security by actively updating their software and implementing multi-factor authentication, for example. Once an organisation has the basics of cyber security in order, they can use the offered tools to further develop their cyber security.
The tools in the catalogue are divided into four categories based on their purpose of use.
- Reducing the likelihood of a damaging cyber incident
- Detecting malicious activity quickly
- Responding effectively to confirmed incidents
- Maximising resilience
EXAMPLES OF THE TOOLS IN CISA’S CATALOGUE:
| Reducing the likelihood of a damaging cyber incident | CISA Vulnerability Scanning | CISA’s tool for mapping the vulnerabilities of user interfaces and services in the public network interface. |
| Detecting malicious activity quickly | Security Onion | An open source tool for threat detection and hunting in network environments. |
| Responding effectively to confirmed incidents | Velociraptor | A tool provided by Rapid7 for collecting and analysing artifacts and hunting for threats. |
| Maximising resilience | HYPR Zero | A platform designed for smaller organisations that delivers passwordless multi-factor authentication. |
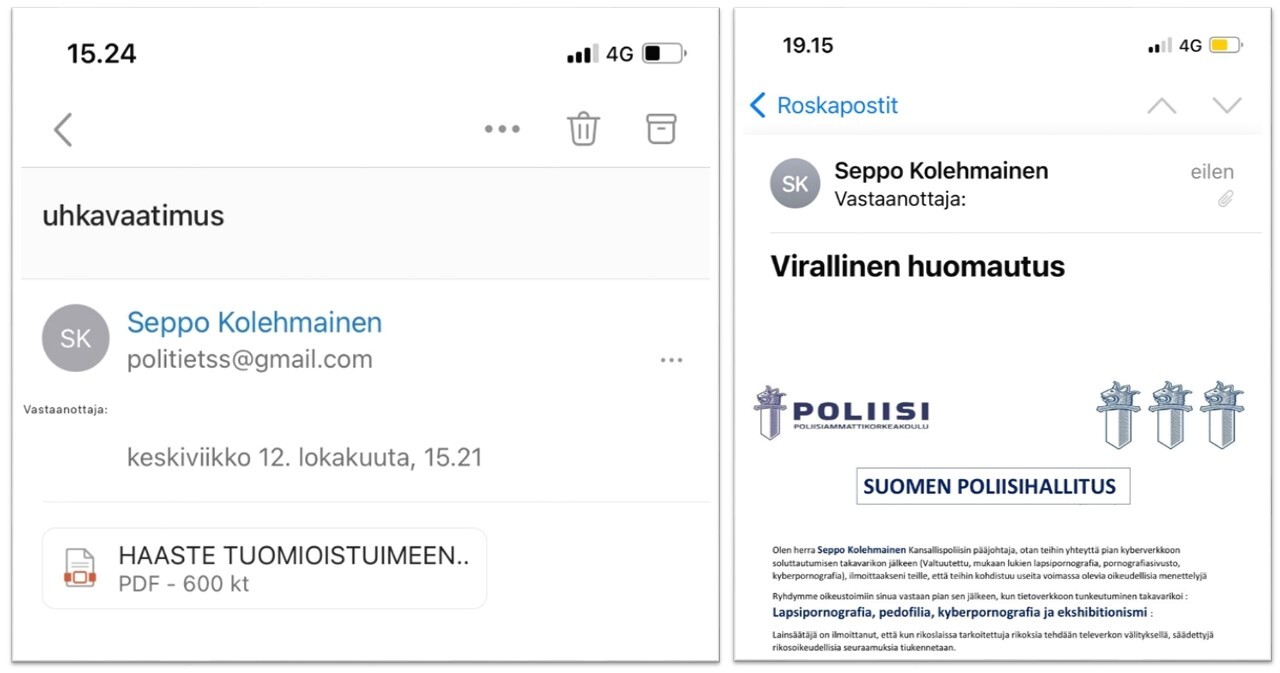
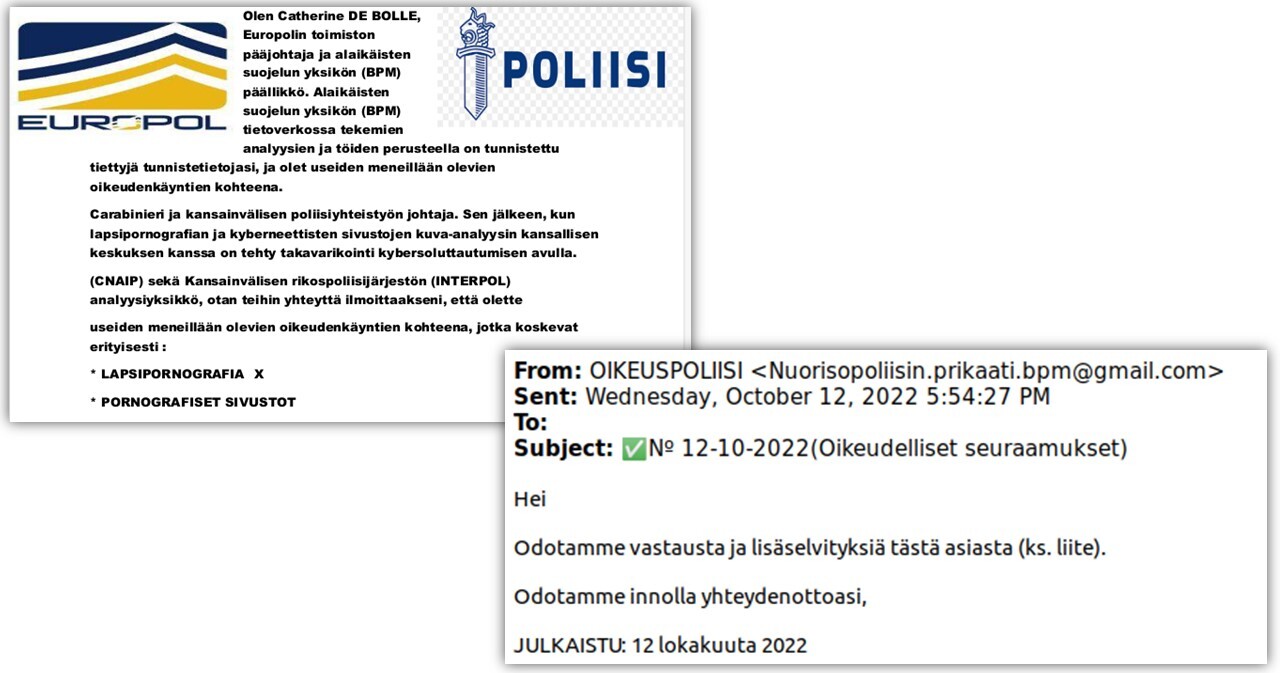
Police impersonation scams on the rise
There are currently a number of new scams going around that involve criminals impersonating various law enforcement agencies in order to blackmail victims with made-up crimes. For a while now, there have been scams going around in Europe involving the spreading of seemingly official and stamped PDF documents supposedly issued by Europol and Interpol, national authorities and police chiefs as email attachments. In Finland, we have seen tailored versions of these scams involving letters seemingly issued by Poliisihallitus (the National Police Board of Finland), Kansallispoliisi (not an actual organisation), Yleinen Hallinto Poliisi (also not an actual organisation) or Poliisiammattikorkeakoulu (the Police University College) with colourful stamps and varying appearances. In some cases, scammers have tried to make their threats more believable by using the names of Europol and National Police Board of Finland directors and the logos of Interpol and the National Cyber Security Centre of the United Kingdom.
Although these scams appear unconvincing, their increase indicates that at least some of them generate enough income to make it worthwhile for criminals to continue spreading them to Finnish addresses. Hopefully active communication and the public highlighting of these scams will improve the awareness of Finnish people and prevent them from falling victim to such scams.
Zalando customer accounts being hijacked and exploited
Over the past week, the NCSC-FI has received numerous reports of user accounts of the online store Zalando being hijacked. The hijacked accounts have been exploited by first upgrading the accounts to Zalando Plus accounts and then making purchases to be delivered to various countries. The online store’s own fraud controls detected the large purchases to be delivered to other countries made with hijacked Finnish accounts, and the accounts were subsequently closed.
The purchases made with the hijacked accounts were paid for using PayPal accounts that had different owners than the Zalando customer accounts. The PayPal accounts may have also been hijacked. Even if the hijacking and exploitation of user accounts does not cause any financial damage to Finnish customers, having your user account closed is still a nuisance.
According to a notification issued by Zalando, the service itself has not been breached. Instead, it is possible that the hijacked accounts were accessed using the same passwords that have been leaked in other major password leaks. In other words, the criminals may have simply been trying out leaked username and password pairs on different services. This is a good reminder not to use the same password on different services, as doing so exposes you to data breaches.
This week’s notable vulnerabilities
For more general information about vulnerabilities and the terminology used, please see our Information Security Now! article ‘NCSC-FI vulnerability coordination in a nutshell.’
Critical vulnerability in Adobe Acrobat and Reader products
CVE: CVE-2022-42339 and CVE-2022-38450, APSB22-46
CVSS: 7.8
Product: Acrobat DC 22.002.20212 and earlier versions,
Acrobat Reader DC 22.002.20212 and earlier versions,
Acrobat 2020 20.005.30381 and earlier versions,
Acrobat Reader 2020 20.005.30381 and earlier versions,
Fix: Update Acrobat DC and Acrobat Reader DC to version 22.003.20258. Update Acrobat 2020 and Acrobat Reader 2020 to version 20.005.30407.
Critical vulnerability in Adobe Commerce and Magento e-commerce platforms
CVE: CVE-2022-35698
CVSS: 10.0
Product: Adobe Commerce version 2.4.4-p1 and earlier versions and version 2.4.5 and earlier versions. Magento Open Source version 2.4.4-p1 and earlier versions and version 2.4.5 and earlier versions.
Fix: Update the vulnerable software to version 2.4.5-p1 or 2.4.4-p2.
Critical vulnerabilities in Fortinet software
CVE: CVE-2022-40684, CVE-2022-33873
Product: FortiOS 7.0.0-7.0.6 and 7.2.0-7.2.1, FortiProxy 7.0.0-7.0.6 and 7.2.0, FortiSwitchManager 7.0.0 and 7.2.0, FortiTester 7.1.0, 7.0.0, 4.2.0, 4.1.0-4.1.1, 4.0.0, 3.9.0-3.9.1, 3.8.0, 3.7.0-3.7.1, 3.6.0, 3.5.0-3.5.1, 3.4.0, 3.3.0-3.3.1, 3.2.0, 3.1.0, 3.0.0, 2.9.0,2.8.0, 2.7.0, 2.6.0, 2.5.0, 2.4.0-2.4.1 and 2.3.0.
Fix: Update FortiOS versions 7.0.0–7.0.6 to version 7.0.7.
Update FortiOS versions 7.2.0–7.2.1 to version 7.2.2.
Update FortiProxy versions 7.0.0–7.0.6 to version 7.0.7.
Update FortiProxy versions 7.2.0 to version 7.2.1.
Update FortiSwitchManager 7.2.0 or 7.0.0 to version 7.2.1.
Update FortiTester to version 7.2.0, 7.1.1, 4.2.1 or 3.9.2
Critical vulnerability in Zimbra Collaboration (ZCS) software
CVE: CVE-2022-41352
CVSS: 9.8
Product: Zimbra Collaboration Suite (ZCS) 8.8.15 and up to 9.0
Fix: Install the Pax utility on the system and restart Zimbra.
Subscribe to the NCSC-FI’s newsletters or RSS feeds to be notified as soon as new information is published.