Information security now!
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 10–16 February 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.

Topics covered in this week’s review
- Widespread and active PowerApps phishing campaign
- Romance scams prevalent on Google Chat as well
- The NCSC-FI participates in numerous cooperation networks – a look at social welfare and health care sector networks
- CERT-EU and ENISA’s report on sustained activity by threat actors
- Numerous vulnerabilities fixed on Patch Tuesday
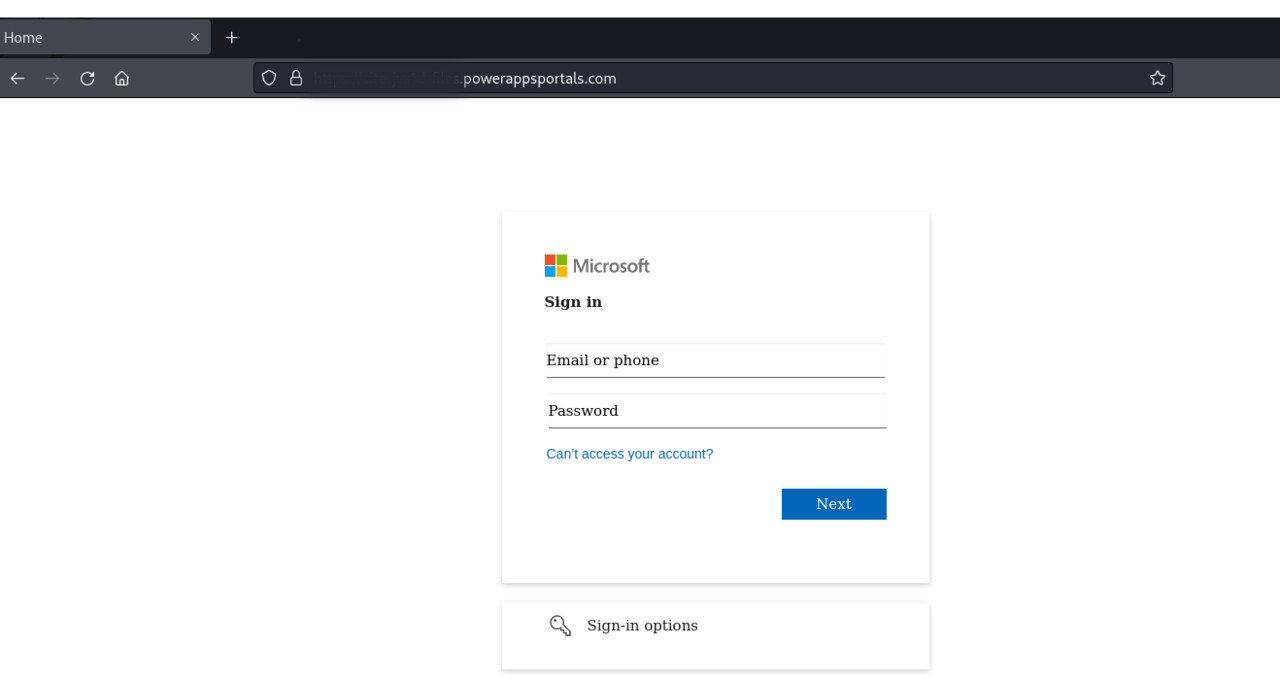
Widespread and active PowerApps phishing campaign
There has been a phishing campaign going around especially among organisations lately that utilises Microsoft’s Power Apps portal. The campaign has already resulted in thousands of phishing messages being sent to numerous different organisations. Power Apps is a software platform that can be used to create websites and other online services, for example.
The phishing messages are being sent from previously compromised email accounts in particular. The messages are often themed around some kind of encrypted or secure email or document. When the user tries to open the message or document, they are directed to a login page asking for their email account username and password. The usernames and passwords entered on these fake login pages are actually sent to the criminals behind the phishing campaign, who may then use them to send out more phishing messages, for example.
The phishing messages and fake login pages are often very convincing. The fake website may even include the logo of the sending organisation or a company providing secure email services. The phishing websites are ‘administered’ via Microsoft’s Power Apps portal, which can prevent them from being flagged as harmful by the user’s browser. Because of this, we urge users to always check whether they are signing in to a genuine website.
The phishing messages are often sent to persons found in the contacts and address books of previously compromised email accounts, which contributes to their credibility and helps them spread quickly. However, this also means that receiving a phishing message does not mean that it was targeted specifically at you. If you receive a suspicious message that seems to include a confidential message or document, you should always check the address of the page that the included link takes you to.
“If the link takes you to a page that you are not familiar with, you should try contacting the sender some other way, such as by calling them, to verify that their message is genuine,” advises Information Security Specialist Olli Hönö from the NCSC-FI.
HOW TO ADDESS THE RELIABILITY OF A WEBSITE
The address displayed on your browser’s address bar tells you exactly what site you are on. The address is the most definitive and surefire way to identify a reliable website. That being said, remembering the address of the real login page and comparing it to that of a potential fake one can be a problem. In unclear situations, you should never enter your username and password. Instead, you should open the correct page via your bookmarks or browsing history, for example. In terms of visuals, a fake login page can be an exact replica of the real page, so you cannot reliably identify a fake page by its appearance alone. In complex phishing scams, the content and appearance of the fake login page may even be copied in real time from the real page, making the fake page impossible to identify based on its appearance.
When it comes to assessing the reliability of a website, there are a number of small factors to consider, both individually and together:
- typos
- suspicious content or probing questions
- the way you accessed the website (email link, redirected from another site, etc.)
- the graphical style of logos and the appearance of the website
- identification of contact information and background operators.
- Did you know that you can report suspicious websites to us?
Romance scams prevalent on Google Chat as well
Despite their long history, online romance scams are still prevalent today, and often carried out across national borders. Romance scams are crimes that anyone can become a victim of. In a typical romance scam, the victim is contacted on a social media platform by an unfamiliar person, who will then start building a relationship with the victim. The scammers behind romance scams are often very skilled at establishing online relationships, and usually their goal is to steal money or obtain personal data from the victim. The scammer may devote a substantial amount of time to gaining the victim’s trust, and in fact the slow pace at which the scam proceeds is often one of the reasons why the victim does not think to question the scammer’s motives.
The perpetrator of a romance scam may initially approach their victim on any social media service. However, the NCSC-FI is aware of cases where the scammers have attempted to move the conversation to a service where they can obtain more information about their victim or to a platform where they can effectively disguise their real identity. One such platform is Google Chat. Using Google Chat only requires the creation of a new Google account, so it is easy for the scammer to create a new account corresponding to their fake identity and thus disguise their real identity. By moving the discussion to Google Chat, the scammer also obtains the victim’s email address, which can often contain information about the victim that the scammer is interested in, such as their first and last name or date of birth. This information can help the scammer learn more information about the victim and more effectively adapt their approach.
The NCSC-FI participates in numerous cooperation networks – a look at social welfare and health care sector networks
Network-oriented cooperation is one of the NCSC-FI’s key service tasks. The NCSC-FI’s networks provide valuable first-hand information about the current state of cyber security and related trends. They also serve as forums for exchanging information about acute cyber threats and long-term preparation between multiple parties.
The cyber security of the social welfare and health care sector is constantly being developed through cooperation on multiple fronts in both Finland and around the world. The NCSC-FI is a member of numerous networks focusing on this kind of cooperation, facilitating some and participating in others as an invited member. A large proportion of this cooperation takes place in volunteer networks. The NCSC-FI also play an important role in the cooperation between public authorities in the social welfare and health care sector.
CERT-EU and ENISA’s report on sustained activity by threat actors
The European Union Agency for Cybersecurity (ENISA) and the CERT of the EU institutions, bodies and agencies (CERT-EU) have jointly published a report to alert on sustained activity by particular threat actors. According to the report, the presented threat actors have been conducting malicious cyber activities against several European Union organisations.
The report highlights several threat actors associated with China, such as APT27, APT30, APT31 and Gallium. Moreover, commercial firms have indicated that threat actors Ke3chang and Mustang Panda are likely operating from the territory of China.
ENISA and CERT-EU strongly encourage all public and private sector organisations in the EU to apply the recommendations listed in the report.
Numerous vulnerabilities fixed on Patch Tuesday
Since 2003, the second Tuesday of every month has been known as ‘Patch Tuesday’ on account of being the day on which Microsoft releases security updates for Windows, Office and other associated products. This regular update schedule facilitates forecasting and the planning of operations as companies can expect to receive updates on a specific day. The same update schedule has also been adopted by several other operators, such as Adobe and SAP. The most recent Patch Tuesday on 14 February 2023 once again included a number of fixes, including ones to three zero-day vulnerabilities that have already been exploited.
A zero-day vulnerability means a vulnerability that the software provider or developer has only just become aware of. In other words, the software provider or developer has ‘zero days’ to fix the vulnerability before it is disclosed.
The most recent Patch Tuesday saw the release of almost 80 fixes by Microsoft alone, in addition to numerous fixes by SAP, Citrix, Adobe and Siemens, among others. We recommend going over the released fixes for any software that you use and installing the relevant updates.
Subscribe to the NCSC-FI’s newsletters or RSS feeds to be notified as soon as new information is published.