Information security now!
Android smart devices pre-infected with malware have been detected in the Finnish consumer market. To enable the installation of malware, a backdoor is already embedded in the devices at the manufacturing stage and cannot be removed. If the manufacturer of the device does not offer an official fix, the device must be disconnected from the network and delivered to a collection point for electrical and electronic waste (WEEE). The National Cyber Security Centre Finland (NCSC-FI) at Traficom urges citizens to check the equipment they have at their disposal and, if doubts arise, to carefully consider purchasing new ones.
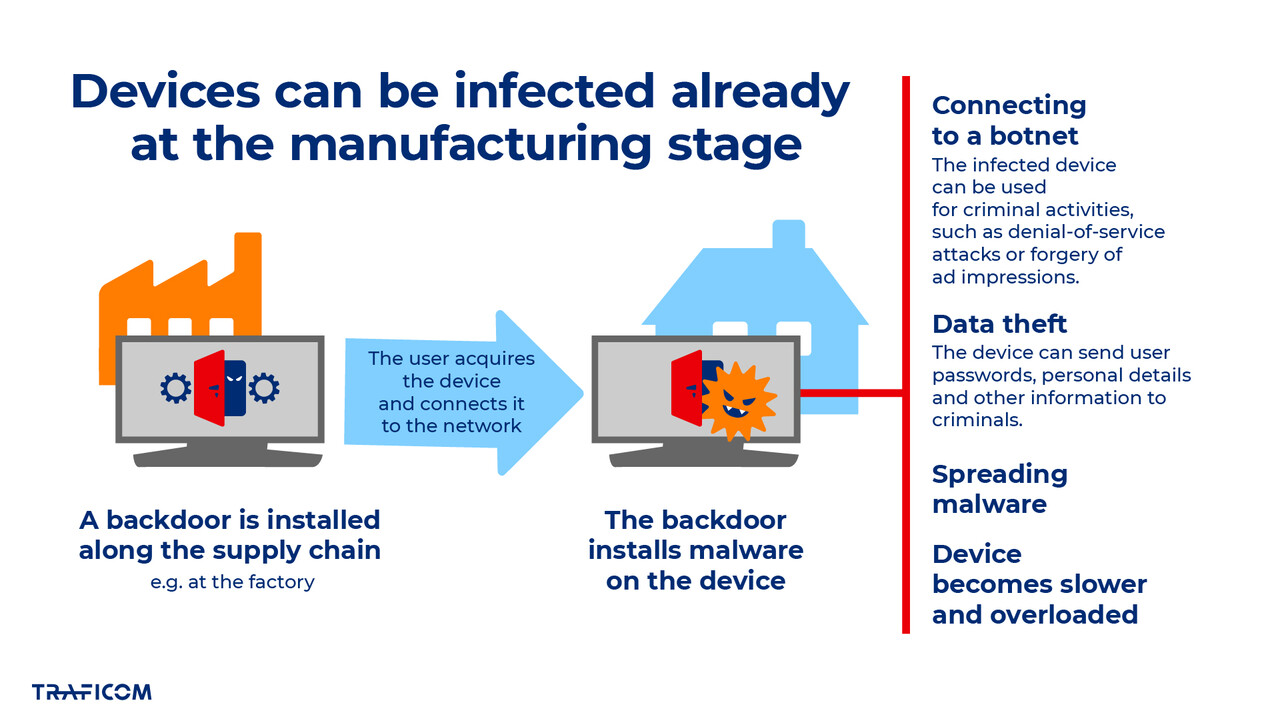
Since the beginning of June, the NCSC-FI has detected an increase in harmful network traffic in Finland related to malware pre-installed on Android devices. The problem particularly affects Android-based TVs, TV boxes and other terminal devices used by Finnish consumers in their home networks. In many cases, the malicious code in question has already been on the device at the manufacturing stage before the user has enabled the device.
In the most serious cases, devices contain malware that cannot be removed because it is embedded in the device's firmware at a write-protected level. In this case, the malicious code cannot be removed by the user through a normal software update or factory reset.
Devices often seem to function normally, but are in fact part of an infrastructure used for criminal activities. Malware can be used to connect a device to a botnet, i.e. a network of infected devices that work together automatically without the knowledge of their owners. Devices connected to a botnet can be used for criminal activities, such as denial-of-service attacks. In addition, malware can collect information about its user, display false advertisements and spread other malware.
Such a malware infection can cause significant harm to the device owner. For example, the device can slow down or become overloaded unnoticed, and the network connection can be used without permission, which may seem like the criminal activity is coming from the user's home network connection and address. In addition, malware exposes personal information – such as passwords, personal details and other information entered on the device – to criminals, leading to potential misuse at a later stage.
BadBox 2.0 malware
Several reports and technical analyses show that one of the key malware in these cases has been BadBox 2.0. It's a malware that's been detected especially on low-cost Android devices from lesser-known manufacturers. BadBox 2.0 can be pre-installed on a device already on the production line, but it can also be shared through malicious applications and suspicious websites.
The number of observations has been increasing globally and, for example, the Estonian Information System Authority RIA wrote in its blog that more than 7,000 infected devices containing Badbox 2.0 have been detected in Estonia.
BadBox 2.0 allows you to remotely start additional modules, collect data and perform other harmful activities without the user's informed consent. It is particularly difficult to detect and practically impossible to remove because the backdoor of the malware is located in the firmware, which cannot be rewritten without the manufacturer's separate actions.
The problem is not limited to individual devices, but relates to a wider phenomenon where certain manufacturers or distribution chains do not ensure sufficient security and quality control in the production of their devices.