Information security now!
This week we talk about a widespread Facebook scam in which accounts are hijacked on the pretext of a made-up monetary prize. Our other topics are new top-level domains and the NCSC-FI’s experts at the Disobey hacker event.

Topics covered in this week’s review
- Social media accounts being hijacked via scam messages
- New top-level domains raise concerns
- NCSC-FI experts’ presentations at Disobey
- Vulnerabilities
Social media accounts being hijacked via scam messages
The NCSC-FI has been receiving increasing numbers of reports of both successful and unsuccessful Facebook account hijack attempts lately.
A Facebook account hijacking attempt often starts with you receiving a message from a Facebook friend via the Messenger app asking for your phone number. If you provide your friend with your phone number, you will soon receive a message from the same friend telling you about a made-up prize draw win. Your friend will claim that in order to redeem the prize, they need a Facebook number code sent to your phone. In reality, the code in question is for logging in to your account, which criminals can use to gain control of your account. If you send the code to your friend, your account will most likely be hijacked by criminals. After hijacking your account, the criminals will edit your account information, such as your account name and contact information. If this happens, you will most likely not be able to regain control of your account without Facebook’s help.
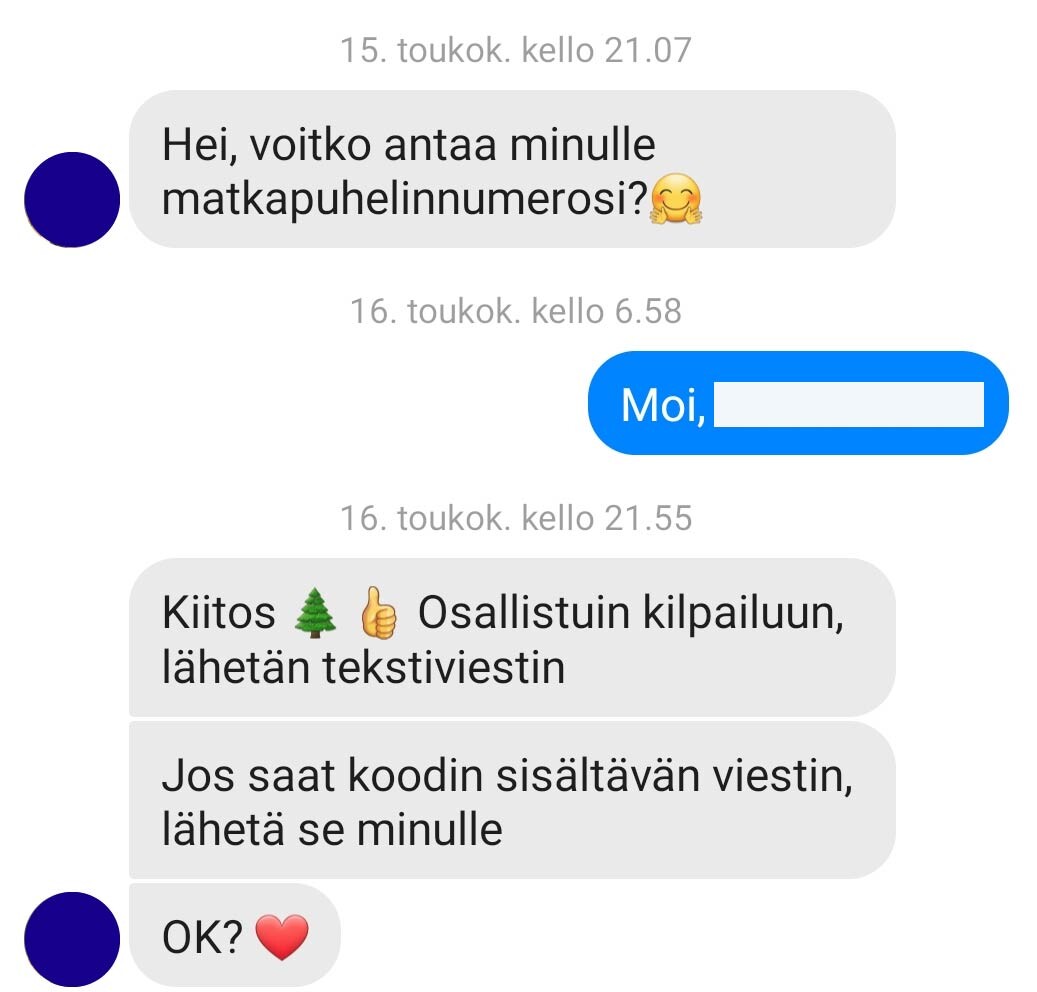
If you receive an unusual or suspicious message from a friend via Facebook Messenger, such as a message asking for your phone number, tell your friend about it using some other means of communication. Your friend should be able to verify whether they actually sent the message and check the status of their own Facebook account, if necessary.
What can I do if my account gets hijacked?
A hijacked Facebook account can only be restored by Facebook. There are also criminals lurking on the internet who prey on people whose accounts have been compromised before. They will claim to be able to help restore a lost account, but in reality their goal is to exploit people whose accounts have been hijacked for monetary gain. As such, you should exercise caution if you decide to seek help for your problem elsewhere on the internet. The only honest way of restoring a social media account is through the official channels of the service in question.
1. Check (External link) whether your account has been compromised. You can also try resetting your password via the ‘Forgot password?’ link on Facebook’s login page (External link).
Facebook’s website (External link) has instructions on how to check whether your Facebook account has been compromised. Follow the instructions to change your password or view recent activity on your Facebook account.
2. Log the hijacker out of your Facebook account.
If you still have access to your Facebook account on your phone, for example, check that the email address and phone number registered to the account are yours. Facebook’s website (External link) has instructions on how to log your account out of Facebook.
4. Warn your Facebook friends.
Warn your friends about what has happened and tell them that any messages they receive from your account are not actually from you. If the hijacker has already made posts or sent messages to your friends via Messenger, warn your friends not to open any links or install malicious software.
5. Report to Facebook that your account has been compromised.
Report to Facebook that your account has been compromised. You can submit your report on Facebook’s website (External link) without logging in.
6. Check whether any malicious applications have been installed on your Facebook account.
Check your Facebook account for any spam posts or installed software. You can do this by following the instructions on Facebook’s website (External link).
7. Check your account security settings.
Go to security settings and enable login alerts. This way you will receive alerts from Facebook about any unrecognised account logins. Enable two-factor authentication. Instructions for this are available on Facebook’s website. (External link)
What happens when an account is hijacked?
Hijacking a Facebook account gives criminals access to personal data, usernames and passwords. Criminals will use hijacked Facebook accounts to hijack other accounts. The friends of the hijacked account will be sent scam messages via Messenger asking for their phone numbers. Your Facebook account data will also be used to log in to other services, so the hijacker may gain access to several services using your account. Because of this, you should always use a different password for every service.
New top-level domains raise concerns
.zip is coming, are you ready?
Earlier this month, Google, among others, launched eight new top-level domains with new domain extensions: .dad, .phd, .prof, .esq, .foo, .zip, .mov and .nexus. Two of these new domains, .zip and .mov, have raised particular attention among information security experts on account of also being known as file extensions: the file extension .zip usually denotes a compressed file, while the .mov file extension often denotes a video file. This fact could potentially be exploited by criminals through the creation of confusing domains, such as phishing sites that deceive users into thinking that they are downloading a file.
The NCSC-FI has so far not received any reports of phishing or scam messages utilising the new domain extensions. However, information security researchers have already discovered some websites using the new domains that attempt to phish for email passwords from visitors. Researchers have also presented other potential ways of using the new domain extensions to deceive users into downloading malicious files.
Normal internet users have no cause for concern, however. That being said, you should keep in mind that links ending with the extension .zip or .mov can now lead to websites instead of files. Different applications may also end up interpreting references to files in messages (such as “file.zip”) as links to websites. If you receive a suspicious message with a link, you should check the URL that the link is actually pointing to. The NCSC-FI has published an article on how to identify suspicious websites by their addresses (External link). You can also report suspicious messages to the NCSC-FI.
NCSC-FI experts’ presentations at Disobey
The annual information security event Disobey was held at Kaapelitehdas in Helsinki in February. The event brings together industry professionals and hacker-minded individuals to enjoy various types of expert presentations and workshops. The many high-quality presentations held at the event also included ones where NCSC-FI experts go to share their knowledge. Recordings of the presentations held at Disobey have now been published on YouTube.
Chief Specialist Jussi Eronen from the NCSC-FI held a presentation on vulnerability coordination in Finland. Through example
Communications Specialist Lotta Sandroos from the NCSC-FI held a presentation based on her master’s thesis, in which she examined information security communications targeted at private individuals. In her thesis, Lotta analysed the NCSC-FI’s communications materials and their frames of communication.
Vulnerabilities
CVE: CVE-2023-33009, CVE-2023-33010
CVSS: 9.8
What: Critical vulnerabilities in Zyxel firewall products – Indications of exploitation
Product: Several Zyxel firewall products
Fix: Software update. For more information, please see our vulnerability bulletin (in Finnish) (External link) and Zyxel’s security advisory (External link)
CVE: CVE-2023-2825
CVSS: 10.0
What: Critical vulnerability in GitLab products
Product: GitLab Community Edition and Enterprise Edition 16.0.0
Fix: Software update, update GitLab to version 16.0.1. For more information, please see our vulnerability bulletin (in Finnish) (External link) and GitLab’s bulletin (External link)
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 19–25 May 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.