Information security now!
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 20–26 January 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.

Topics covered in this week’s review
- “Is it you in this video?” – beware of the scam currently circulating on Facebook
- Denial-of-service attacks decreasing
- The information security of products on the market varies
- Vulnerabilities
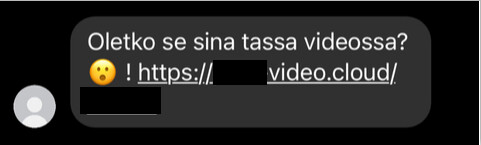
“Is it you in this video?” – beware of the scam currently circulating on Facebook
Lately the NCSC-FI has been receiving reports of scam messages going around on Facebook aimed at phishing for the recipients’ account information. Similar scam messages have been circulating for years now in many different languages, including Finnish. A characteristic that these scam messages have in common is that they attempt to win the recipient’s trust by being seemingly sent by persons who the recipient already knows.
The message will usually arrive from the Facebook account of a person familiar to the recipient and ask “Is it you on this video?” In addition to the question, the message will include a link that leads to a phishing site. On the phishing site, the user is asked to enter their Facebook login information. If they do, their login information ends up in the hands of the scammer, who will then sign in to the account and proceed to spread the same scam messages to the victim’s Facebook friends.
If you have received a message like this, proceed as follows:
- Do not open the link in the message, and do not enter your login information on the page that it opens.
- Delete the message to avoid opening the link in future.
- If possible, contact the sender some other way and tell them that their account has been compromised.
If you have entered your login information on a phishing site or are worried that your account may have been compromised, try to sign in to Facebook on some other device and change your password as quickly as possible. It is also a good idea to warn your Facebook friends that your account may have been compromised and they may receive scam messages form your account. If you have not enabled multi-factor authentication yet, you should do so. In many cases, multi-factor authentication can prevent third parties from signing in to your user account. If you cannot access your account on another device, contact Facebook’s customer support.
Denial-of-service attacks decreasing
December 2022 accounted for 25% of all the denial-of-service attack reports received by the NCSC-FI in 2022, while the last quarter of the year accounted for over half of the year’s reports. In January, the NCSC-FI has received a notably lower number of reports than at the end of the year.
A denial-of-service attack is a simple but flashy attack technique. Denial-of-service attacks are also often covered by media outlets. Making an organisation’s public service, such as a website, temporarily unavailable gives the impression of an effective attacker, even if the actual impacts of the attack remain minor. The fact is that besides a brief disruption in service, denial-of-service attacks seldom have any other impacts.
The NCSC-FI recommends organisations’ administrations to prepare for denial-of-service attacks by e.g. considering the following questions:
- Have the most critical services been identified and protected against denial-of-service attacks?
- Have the response processes to denial-of-service attacks been defined and practised?
- Have you considered how customer communication would be organised in the event of a cyber incident?
- Does the response process include reporting the incident to the NCSC-FI and the police?
More information
The information security of products on the market varies
During the past week, Finnish newspaper Ilta-Sanomat (External link) reported on a vulnerability discovered in a webcam by information security researcher Jarkko Vesiluoma. The fact is that the information security of the various smart devices sold in shops and online varies, with the webcam highlighted in Ilta-Sanomat’s article being a good example: it included a backdoor that makes is possible to hijack the webcam remotely once it has been connected to the internet. Hijacked devices can be used by criminals for network attacks, for example. The device mentioned in the article is currently being investigated by the importer, and Finnish retail chain S-ryhmä reports in the article that it has removed the device from sale. Unfortunately, some network devices are simply poorly designed from an information security perspective. Of course there are also many types of users – some will connect devices to the internet without giving the matter much thought, while others will immediately change default passwords and configure devices to their liking.
The warranties that products have also vary. A product might be adequate in terms of information security now, but what about five years from now? How many years of information security updates does the manufacturer guarantee for the product? Luckily the EU has stepped up to the challenge and decided to implement a regulation imposing information security requirements on smart devices. In response, manufacturers, importers and retailers should take steps to ensure the information security of their products now before the regulation goes into effect.
Report a vulnerability
A vulnerability means any weakness that can potentially cause damage and that can be exploited to cause damage. Vulnerabilities can be present in information systems, software, devices, processes and household automation, in addition to which they can also arise as a result of people’s actions. Have you ever wondered where you may report a vulnerability you have discovered? Would you like to submit a report, but cannot find instructions on how to do so? Perhaps you have heard that there are rewards for reporting vulnerabilities, but you do not know how the process works? Not to worry: we will tell you what to do.
Vulnerabilities – how to report them correctly.
Are you familiar with the Cybersecurity Label?
The Cybersecurity Label (External link) granted by the Finnish Transport and Communications Agency Traficom’s National Cyber Security Centre Finland indicates that the product or service bearing it has been designed to be information secure and meets Traficom’s information security requirements. The label is used on smart consumer devices that can be connected to the internet, meaning so-called IoT devices. These include smart bracelets and household routers, for example.
The current and future problems associated with devices connected to the internet were also explored in Ilta-Sanomat (External link) this past week. The NCSC-FI’s recommendation is that users should demand information security from the products that they purchase now and in the future. Better information security also means a longer service life!
Checklist for the secure use of smart devices
Here are some easy ways to improve the information security of your smart devices:
- When setting up a new device or service, create a sufficiently strong password for it. Use a different password for every service.
Read more: The longer the better — How to create a strong password - Do not ignore software updates. Software updates also contain important security updates.
Read more: Remember to update devices, software and applications! - An old product may present an information security risk if the manufacturer is no longer providing security updates for it. Check the life cycle of the product on the manufacturer’s website.
Read more: How to safely recycle your devices (article in Finnish) (External link) - Choose a product that has been granted an information security certificate, if possible. Information security certification is constantly being developed, with more and more certified products available on the market.
Vulnerabilities
CVE: CVE-2022-31706, CVE-2022-31704, CVE-2022-31710, CVE-2022-31711
CVSS: 9.8
What: Several critical vulnerabilities that should be patched as soon as possible.
Product: VMware vRealize Log Insight
Fix: Update available
Subscribe to the NCSC-FI’s newsletters or RSS feeds to be notified as soon as new information is published.