Information security now!
Criminals are now targeting companies’ and associations’ Facebook accounts. The attacks involve messages sent via Messenger claiming that the user’s account will be closed due to a copyright infringement, for example.

Topics covered in this week’s review
- Companies’ and associations’ Facebook accounts being hijacked
- PDF attachments included in scam messages should be handled with caution
- Our new guide for planning information security training
- Critical vulnerability in Qlik Sense
Companies’ and associations’ Facebook accounts being hijacked
Social media services also interest criminal actors to the extent that user accounts and login information are regularly hijacked. Right now, criminals are targeting accounts used to manage companies’ and associations’ Facebook pages, as evidenced by the fact that the NCSC-FI has been receiving numerous reports of Facebook account breaches.
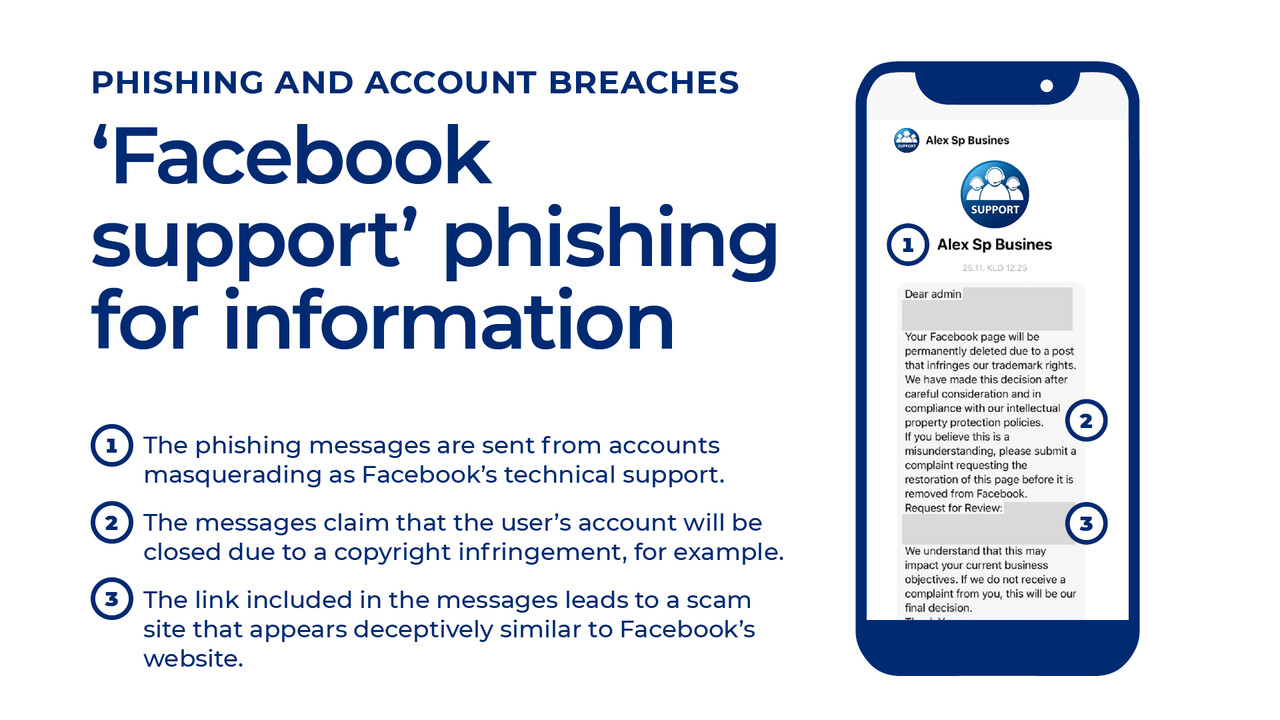
The attacks involve criminals impersonating a representative of the social media service, such as ‘Meta Business Support’, and sending messages via Messenger claiming that the victim’s account or page will be closed or suspended unless they react to the presented demands. The messages include a link that the victim is supposed to follow. The link will typically open a fake page disguised as a login page, the purpose of which is to get the victim to enter their login information or verification code, which are then relayed to the criminals. These allow the criminals to hijack the victim’s Facebook account, which they can use for spreading fake ads, subscription traps and other criminal activities.
The fraudulent Messenger messages often address the victim as ‘Dear admin ...’ and start with a six-character code, such as ‘Track#12X34Y’. The reason given for the message is that the victim has posted something on the service that violates copyright or advertising rules. The included link does not lead to a Facebook address, but rather to an address that looks very similar, such as ‘facebookjob’.
Do not trust the first search result
The aim of the scam messages is to scare and alarm the victim so that they will react quickly and carelessly. Some of the recipients of the scam messages have sought help by searching for customer service departments on search engines, only to end up finding another scammer on top of the search results. Various Finnish word combinations similar to ‘asiakaspalvelu’ (‘customer service’), such as ‘suomiasiakaspalvelu’, ‘suomenasiakaspalvelu’ and ‘asiakaspalvelufacebooksuomi’, may, depending on the search engine, lead to fake customer service departments, which will not hesitate to deceive the victim further.
Contact the police
If you have lost money to internet fraud, your first step should be to immediately contact your bank. In the best case scenario, your bank will be able to stop the criminals from taking your money.
Right after this, you should report the incident to your most important cooperation partners and consider whether you need to provide information about it to the public. Internet fraud is a crime that should be reported to the police. If your organisation has suffered a data breach, you should also report it to the NCSC-FI. If your organisation’s confidential data or personal data has been leaked to a third party, you should also report the incident to the Office of the Data Protection Ombudsman.
PDF attachments included in scam messages should be handled with caution
Extortion messages sent by scammers impersonating the police have been circulating for a long time, both with and without attachments. We last wrote about these types of extortion messages back in August in our weekly review 33/2023 (External link).
In the past, the attachments accompanying the extortion messages have not contained any additional hidden content. However, the NCSC-FI has now been receiving reports of individual scam messages with PDF attachments containing executable javascript code. The codes included in the samples analysed thus far do not yet do anything more dangerous than open a print window that the user can use to print out the document. Whenever a PDF or Office document included as an attachment in an unknown email message asks for permission to execute commands, it is always best to deny the request, however, as the commands can also start up malware.
Scam messages sent under the name of various real and made-up law enforcement authorities may not seem very believable to people who are familiar with the services of Finnish authorities. However, the persistence of these types of scam messages speaks to the fact that sending them is profitable to criminals.
Our new guide for planning information security training
An organisation’s information security is often seen as a technical matter based on information systems. However, these systems are used by people – the organisation’s entire personnel. As such, personnel plays a major role in the building and upholding of an organisation’s information security culture. The fact is that information security is not dependent on any one person or information system: it is an organisation-wide matter that encompasses not only technical mechanisms, but everyday things as well.
Making information security awareness a common priority improves an organisation’s overall level of information security and makes the organisation more resistant to cyber attacks. Mistakes will always happen, but equipping personnel with an appropriate level of information security awareness and the right kind of operating models allows an organisation to prevent mistakes before they happen and minimise their impacts.
Organisations can increase the information security awareness of their personnel through information security training and cyber exercises, for example. Last week, the NCSC-FI published a new guide that provides organisations with tips for planning information security training. The guide provides summaries of themes that personnel should be trained on as well as tips for the actual planning process.
Critical vulnerability in Qlik Sense
CVE: CVE-2023-48365
CVSS: 9.6
What: Exploiting the vulnerability allows an attacker to elevate their privilege and execute arbitrary code on the backend server hosting the Qlik Sense repository. The vulnerability is known to have been used for ransomware attacks.
Product: Qlik Sense Enterprise for Windows
Fix: Installing a patch that fixes the issue
Read more (in Finnish): Vulnerability bulletin 28/2023 (External link)
About the weekly review
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 24–30 November 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.