Information security now!
This summer has seen the public disclosure of several critical software vulnerabilities. Has your organisation made sure to keep systems updated and patched even during the summer holidays?

Topics covered in this week’s review
- Updating and patching systems quickly is critical even during holiday periods
- Police impersonation scams rearing their heads again
- Save the date: Tietoturva 2023 information security seminar to be held on 12 October
Updating and patching systems quickly is critical even during holiday periods
This summer has seen the public disclosure of an exceptionally high number of critical software vulnerabilities. Such vulnerabilities are constantly being sought out by software developers, free information security researchers, information security firms and criminals carrying out cyber crimes. When a new vulnerability is discovered by a benevolent party, a patch addressing it can usually be distributed to users before the vulnerability is publicly disclosed. But when a vulnerability is discovered by criminals, their top priority is to try to exploit it before it can be patched.
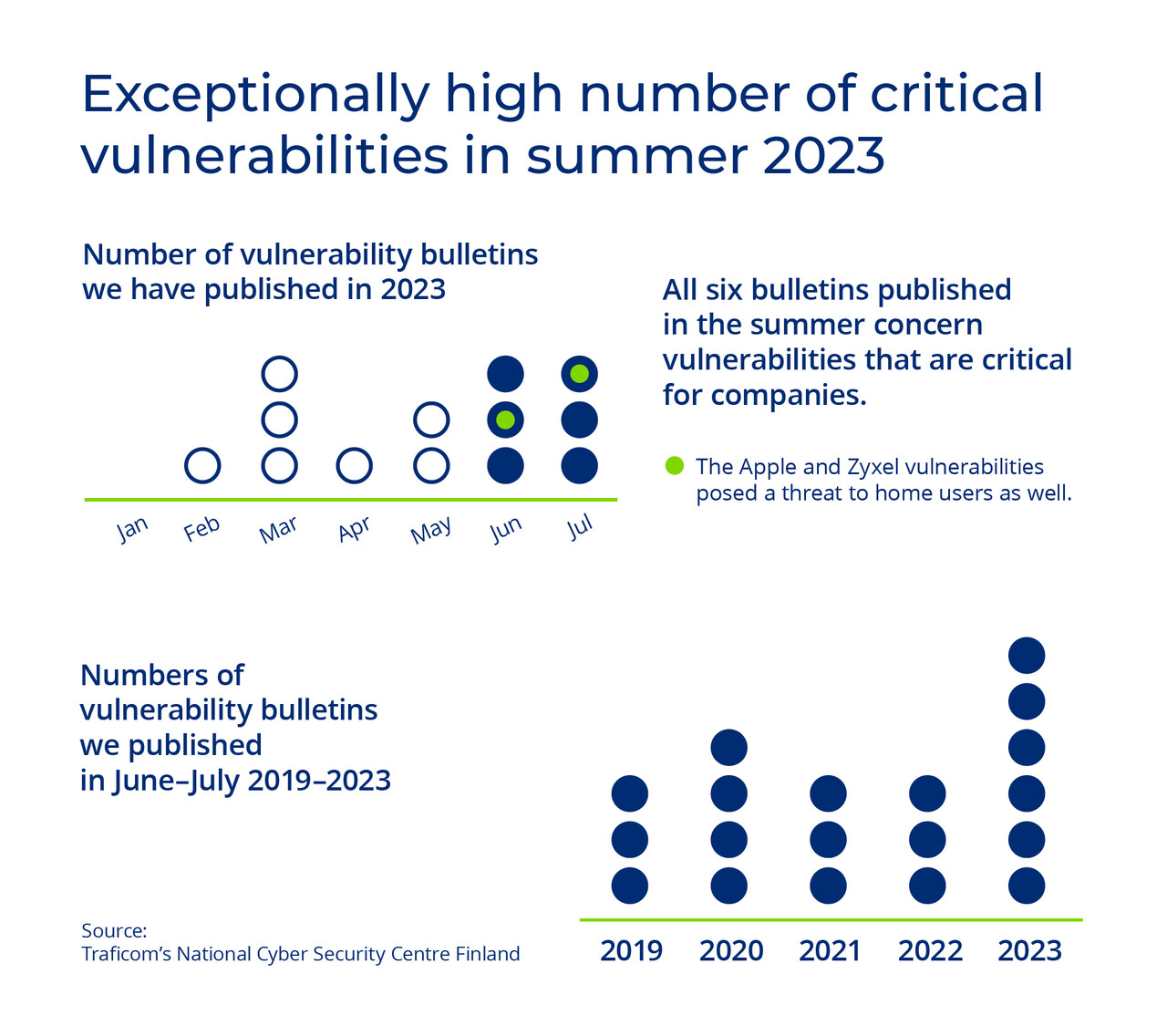
Whenever new vulnerabilities are publicly disclosed, criminals will immediately proceed to actively exploit them. When a vulnerability is patched, criminals start scouring the network for systems that have not been patched yet and focus their attacks on them. Criminals will also often share malicious code exploiting vulnerabilities amongst themselves online, allowing more and more criminals to exploit a given vulnerability to carry out cyber attacks. Because of this, the importance of patching systems quickly cannot be overstated.
The responsibility for updating and patching an organisation’s systems lies with the organisation itself. Patches addressing critical vulnerabilities are distributed around the year, which is why organisations also need to make substitute arrangements for holiday periods. All organisations need to be prepared to quickly patch their systems or take them offline until they can be updated when necessary. Whenever patching is delayed, the likelihood of the unpatched system suffering an attack exploiting a vulnerability increases.
Do not ignore your update process during the summer (article in Finnish) (External link)
In most cases, simply updating systems is not enough to ensure their security. Publicly disclosed vulnerabilities are aggressively exploited, and sometimes a vulnerability can be exploited without immediately disrupting the compromised system. Criminals can e.g. exploit vulnerabilities to install backdoors, giving them covert access to the compromised system. These backdoors can be used to carry out attacks even after extended periods, and simply updating the compromised system will not get rid of all of them. Because of this, organisations should not only keep their systems updated, but also regularly check them for any attacks that may have already taken place.
The NCSC-FI has also surveyed vulnerable systems in order to notify their owners about vulnerabilities. In July, we reached out to over a hundred organisations about a vulnerability discovered in Citrix Netscaler Gateway and ADC software and the patch addressing it. Globally, recorded cyber attacks exploiting this vulnerability number in the thousands. Seeing as how the vulnerability and the malicious code exploiting it have been publicly shared for a relatively long period of time already, it is safe to assume that nearly every unpatched system has been attacked, if not breached by now.
More information
The NCSC-FI publishes a daily vulnerability digest in which we list the latest publicly disclosed vulnerabilities. For the most notable vulnerabilities, we also publish separate vulnerability bulletins. That being said, for the most up-to-date information on updates and patches for the software and devices that you use, you should aways turn to the manufacturer of said software or device. Manufacturers notify their customers about any updates and patches that they release, and widely used devices, such as smartphones, are designed to be quick and easy to update. Updating and patching more complex systems is typically more demanding and should thus be planned in advance.
Police impersonation scams rearing their heads again
The prolonged absence of police impersonation scams has seemingly come to an end, with the NCSC-FI having received a number of reports of these types of scams during the past week. The scam messages in question were sent to potential victims via email and included a PDF attachment. The PDF file was titled "SYYTTÄMISMÄÄRÄYS" (Finnish for “prosecution order”) and included the stamps of the Finnish police, the Finnish Ministry of Justice, Interpol and the National Cyber Security Centre of the United Kingdom.

Save the date: Tietoturva 2023 information security seminar to be held on 12 October
Last year, the Tietoturva information security seminar organised by Traficom’s National Cyber Security Centre Finland and the National Emergency Supply Agency was attended by over 1,000 people on-site and remotely. The popular seminar will be held again this year on Thursday 12 October 2023 at 9:00–16:30.
This year, the seminar will feature discussion about the future of cyber security and cyber threats. Rapidly advancing technologies, such as artificial intelligence, present not only new opportunities but also new kinds of threats. What are these threats and how can you prepare for them? Join the seminar to hear what Finnish and international industry experts have to say.
Save the date – event registration will open in August. We will be publishing more information about the event and featured speakers on our website as the seminar programme is updated.
More information
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 11–17 August 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.