Information security now!
You should not trust search engine results uncritically. Even this week, fake search results have been seen leading to phishing pages. This week we also report on how the NATO Summit in Finland went from a cyber security perspective. We remind you of the importance of secure management of network edge devices and of timely security updates. We also invite you to learn about the new regulatory requirements in the CRA (Cyber Resilience Act).

NATO summit in Finland goes off peacefully
Finland and Estonia co-hosted the NATO Baltic Sea Region Summit in Helsinki on Tuesday this week. The meeting discussed the protection of critical underwater infrastructure in the Baltic Sea.
The NCSC-FI raised its preparedness for possible cyber breaches or other disruptions in the run-up to the summit. Similar high-level state visits in the past may have seen, for example, protest-inspired denial-of-service attacks or phishing campaigns, but this time the situation was generally calm from a cyber security perspective.
As part of the increased preparedness, information exchange with other authorities was intensified, and other national and international networks were also mobilised when special monitoring was launched. Cooperation and exchange of information with stakeholders is a key part of the NCSC-FI’s approach to preparedness in different situations.
Underwater infrastructure has been in the spotlight in recent months with several damaged submarine cables in the Baltic Sea. A declaration issued by the Office of the President of the Republic of Finland at the end of the summit outlines a number of measures to protect critical infrastructure in the Baltic Sea region. [1, 2]
[1] https://www.presidentti.fi/en/security-in-the-baltic-sea-region-to-be-strengthened-by-military-presence-and-technological-innovations/ (External link)
[2] https://www.presidentti.fi/joint-statement-of-the-baltic-sea-nato-allies-summit/ (External link)
Network device management interfaces should be removed from public networks
In particular, the NCSC-FI recommends that users of Fortinet's network products immediately check and, if necessary, block the management interface of the products they use from being visible on public networks.
Last week, Fortinet announced a critical zero-day vulnerability [3], which the data security firm Arctic Wolf reported having previously identified [4]. The vulnerability allows penetration of FortiGate devices through the management interface, if publicly available. The campaign has been opportunistic in nature, and there is reason to believe that all the management interfaces available online have been hacked. Fortinet device owners are advised to scan their device and their environment for signs of a breach and its traces.
If you observe unusual or unexplained behaviour, please contact NCSC-FI, for example using our form [5].
The directive to remove management interfaces from the public network obviously also applies to products other than Fortinet's, as this completely closes one potential and risky entry vector for cybercriminals. We strongly recommend limiting the availability of management interfaces if at all possible.
[3] Critical vulnerability in Fortinet’s FortiOS and FortiProxy products (External link)(CVE-2024-55591) (in Finnish)
[4] https://arcticwolf.com/resources/blog/console-chaos-targets-fortinet-fortigate-firewalls/ (External link) (External link)
[5] Inform us of data security violations (External link)
Beware of fake search results
Criminals feed search engines with malicious search results by buying advertising space on search engines. Such search results lead to a fake page that looks like an authentication service, where bank credentials are harvested. This week, fake search results have been reported using the search term ‘Traficom’. Traficom reported this in a disruption notification (in Finnish). (External link)
Similar paid, but fake, search results have been seen in the past for different search terms used by different banks and authorities. The NCSC-FI and interested parties have contacted the companies that run the search engines and have managed to get the phishing pages and malicious ads that lead to them removed from the web.
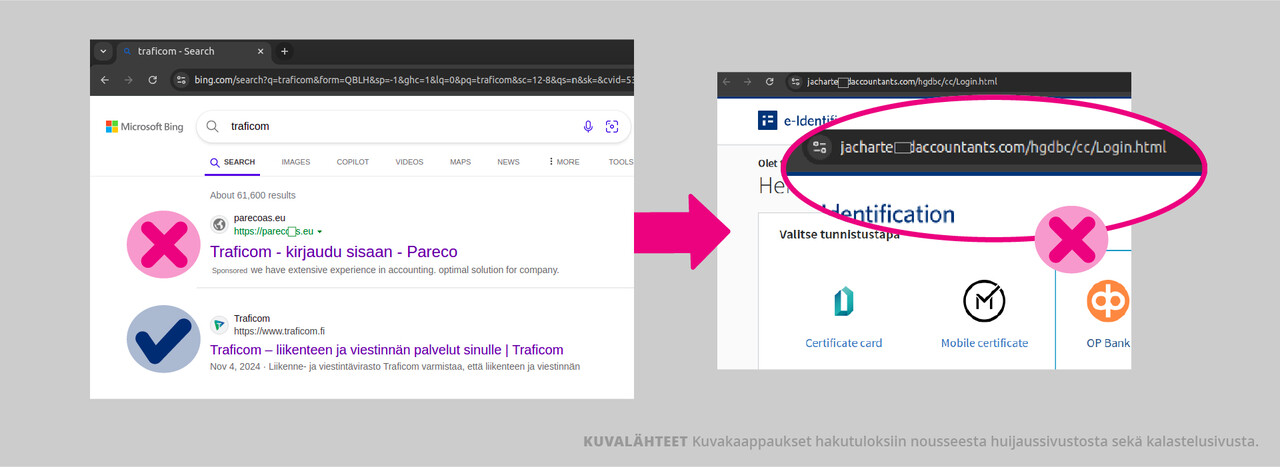
How can you protect yourself from bank fraud?
You can lose your online banking credentials to criminals if you accidentally log in to a phishing page that looks like your own online bank. You usually end up at a fake page by following a fake link. Fake links are usually distributed in scam emails or, as in this case, through rigged search engine results.
The address bar of a web browser also serves as a search engine input, if you just enter a simple name, e.g., "Traficom" without the .fi extension of the web address. The browser automatically returns search results even if the address of the online bank is misspelled, e.g., "tarficom.if" or "pankkki.fi". In this case, phishing pages can also be included in the results.
When you go online, please consider the following:
- Bookmark the government services and online bank that you use frequently in your browser
- In the address bar of your browser, make sure that the address is the service’s own address
- Don't rely blindly on search engine results
- Don't go to login pages from email links or text messages
- Use your bank's mobile app for banking
- Long live that little difference: the address of a scam bank is different from the correct address

December 2024 Cyber Weather published
- In December, data breaches and ransomware attacks against network edge devices were detected. Data phishing in the name of authorities and various scams also continued. The effective cooperation between authorities and the high level of preparedness of society was again demonstrated by the investigation of the submarine cable incident of 25 December 2024.
- Read more about December’s Cyber Weather here: Cyber Weather, December 2024 (External link)
Join us for the CRA morning on 23 January
- The CRA (Cyber Resilience Act) brings new regulatory requirements that will affect many organisations. How can businesses prepare for these changes?
- Join our webinar on 23 January from 8.30 to 9.00 a.m.
- Qt Group's Director of Portfolio Santtu Ahonen will share practical tips on meeting regulatory requirements.
Recently reported scams
- In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or payment card information.
- File a police report. You can file a police report online (External link).
- You can also report the incident to the NCSC-FI. (External link)
- Guidance for victims of a data leak (External link)
Recognise online scams and protect yourself from them
Vulnerabilities
CVE: CVE-2024-55591
(CVSS: 9.6)
What: Critical vulnerability in Fortinet's FortiOS and FortiProxy products
Product: The vulnerability applies to FortiOS versions 7.0.0 - 7.0.16, and FortiProxy versions 7.2.0 - 7.2.12 and 7.0.0 - 7.0.19
Repair: Upgrading a vulnerable software version to the latest version offered by the manufacturer.
For more information, see the vulnerability bulletin 3/2025 (External link)(in Finnish).
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (reporting period 10–16 January 2025). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cybersecurity specialists to regular citizens.