Information security now!
This week, we report on scam calls made from foreign numbers. We also highlight a surge in M365 account compromises, the entry into force of a new regulation concerning radio equipment, and an upcoming webinar on software security to be held in the autumn. In addition, we have published the July edition of Cyber Weather, and in this week’s malware review, we take a closer look at the 911 S5 malware.
Topics covered in this week’s review
- Scam calls on the rise – callers impersonate banks and authorities using foreign numbers
- Microsoft 365 credential phishing on the rise – always check the login page URL
- New requirements to improve information security in smart devices
- Topical webinar on software security, 9 September 2025
- Malware review: 911 S5

Scam calls on the rise – callers impersonate banks and authorities using foreign numbers
Over the summer, the NCSC-FI has received an increasing number of reports about scam calls in which the caller may claim to represent a bank or an authority. These calls often come from foreign phone numbers.
Such calls rarely originate from Finnish numbers, as Traficom and telecommunications operators have worked together to block number spoofing. Read more on Traficom’s website:
A typical scam begins with a claim that suspicious activity has been detected on the recipient’s bank account or that their personal data has been used in criminal activity. The caller tries to create a sense of urgency and pressures the recipient to provide online banking credentials, payment card details, or to install remote access software.
Scam calls are a common example of social engineering, where criminals attempt to deceive people into disclosing sensitive information—such as banking credentials or passwords—or even into transferring money. Social engineering poses a significant cyber security threat because it exploits human trust and behaviour rather than technical vulnerabilities.
The police and banks remind everyone that they never request online banking logins, credentials or software installations over the phone. Unexpected calls from foreign numbers should always be treated with caution.
If you suspect a scam, hang up immediately and contact your bank or the relevant authority directly using their official contact details. Suspicious calls can be reported to the NCSC-FI and the police. If you have disclosed your banking details during such a call, contact your bank and the police immediately.
Your best protection is your own judgement: never share your information with anyone, no matter how convincing the story may sound.
Microsoft 365 credential phishing on the rise – always check the login page URL
After the summer holidays, your inbox may be full of unread emails. In a rush, it’s easy to click on links without thinking twice. That’s why it’s important to pause for a few seconds and check where you’re logging in—are you on a genuine Microsoft 365 page or a phishing site run by criminals?
The NCSC-FI has received several reports of phishing emails targeting Microsoft 365 credentials. In these cases, the message appears to come from a known partner or colleague. The subject line may say something like “Person X has shared a document with you”, just like in legitimate SharePoint or OneDrive notifications. The link in the message often points to a document shared from the organisation’s Online SharePoint or OneDrive service, making it look harmless. However, the phishing link is embedded inside the shared document and redirects the user to a fake Microsoft 365 login page designed to steal credentials.
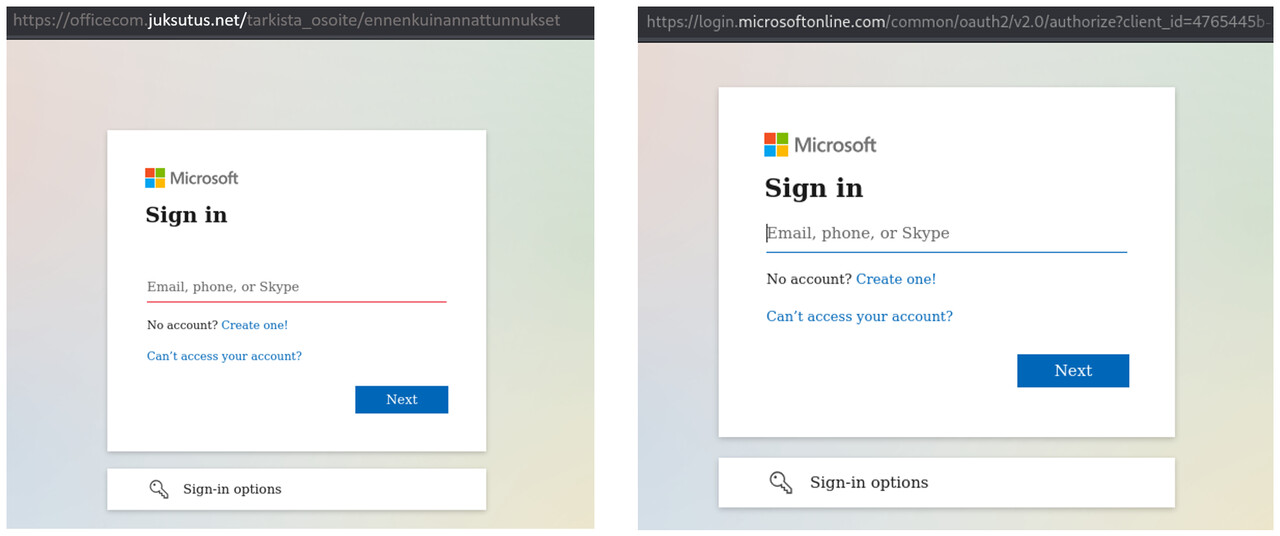
In some cases, an Adversary-in-the-Middle (AiTM) technique has been used, which can bypass multi-factor authentication. Learn more about AiTM attacks and how to protect against them:
New requirements to improve information security in smart devices
From August 2025, the EU will tighten information security requirements for radio equipment. Only devices that meet the new requirements may be placed on the EU market. The rules apply to smartwatches, smartphones, baby monitors and other internet-connected devices. The aim is to protect users from privacy violations and online fraud.
Traficom will supervise compliance and ensure that manufacturers, importers and distributors meet the requirements. If necessary, non-compliant products can be withdrawn from the market.
As an additional layer of protection, the EU’s Cyber Resilience Act will apply from 2027. It will require, for example, automatic updates and secure default settings. From September 2026 onwards, manufacturers must report actively exploited vulnerabilities and incidents having an impact on the security of products on the EU market to both the NCSC-FI's CSIRT unit and ENISA. They must also inform consumers about security vulnerabilities in their devices.

Senior Specialist Heikki Juva also gave a talk on EU regulation and device security at the Disobey hacker event in February 2025. The talk is available in English on YouTube:
Topical webinar on software security, 9 September 2025
We have seen cautionary examples in Finland as well of what can happen when software security fails. The consequences can be serious, ranging from personal data leaks to disruptions in services critical to society. Software security is not just a technical matter; it is a key element of societal resilience and public trust—in short, security of supply.
You are warmly invited to a webinar on 9 September, from 9.00 to 11.00, where we will explore what kinds of skills are needed—now and in the future—to ensure the security of software systems.
Speakers include experts from the National Emergency Supply Agency, the NCSC-FI at Traficom and Solita.
Malware review: 911 S5
911 S5 is one of the largest malware campaigns of recent years. It is particularly known for its ability to hijack users’ devices into a vast proxy server network (botnet), which criminals have used to conceal scams, identity theft and other forms of cybercrime.
The malware often spreads bundled with free software such as VPN tools or file management applications. When the victim installs the compromised software, 911 S5 quietly installs itself in the background. It then turns the device into part of a botnet, which is sold on to criminals as a service (residential proxy-as-a-service). Victims usually notice little to nothing unusual—apart from a possible slight decrease in performance—while the device otherwise functions normally.
To protect yourself, avoid installing software from untrusted sources and use up-to-date anti-malware protection. Organisations should also monitor their network traffic for unusual outbound connections.
Read more:
July’s Cyber Weather report published
From a cyber security perspective, July began under mostly fair skies, even if there were no signs of a real heatwave. Towards the end of the month, however, the overall outlook turned gloomier.
Various scams and phishing attempts remained widespread throughout July. At the end of the month, a particularly aggressive extortion campaign clearly stood out from the rest.
On the malware front, there was some positive news: detections of BadBox 2.0 dropped significantly from their June peak. Nevertheless, the threat posed by this malware has not disappeared.
July also brought serious vulnerabilities and individual data breaches, which contributed to a deterioration in the overall cyber security situation.
As always, this edition of Cyber Weather also reviews the Top 5 threats.
Read the full Cyber Weather report here:
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or gotten hold of your payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI. (External link)
- Instructions for victims of data leaks (External link)
Learn how to detect and protect yourself against online scams
About the weekly review
This is the weekly review of the National Cyber Security Centre Finland (reporting period 8–14 August 2025). The purpose of the weekly review is to share information about current cyber phenomena. The review is intended for everyone from cyber security professionals to ordinary people.