Information security now!
This week’s review covers scam text messages sent in the name of child protection services, used by criminals to phish for information. We also report on Teams call scams, where criminals impersonate IT support in an attempt to gain access to employees’ computers. In addition, malware disguised as PDF editing software has been circulating, enabling criminals to steal information or take over systems. This week’s malware review focuses on Avalanche.
Topics covered in this week’s review

Scam text messages sent in the name of child protection services
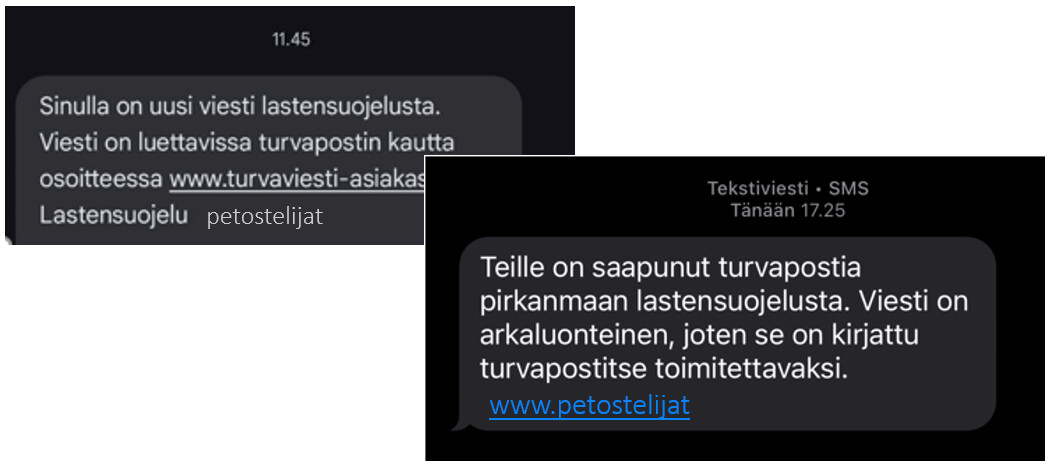
Criminals are currently distributing scam text messages in which they pose as, for example, social workers and refer to child protection services. Victims have included individual organisations, with financial losses ranging from several thousand euros to as much as one hundred thousand euros.
The messages may appear genuine but are designed to cause concern and trick the recipient into opening malicious attachments or links. In the latest scam, criminals have attempted to steal victims’ online banking credentials or mobile certificates.
Messages referring to child protection can be particularly sensitive, which makes them an effective tool for fraud attempts. Organisations and citizens should remember that authorities never send unexpected messages containing suspicious links or attachments. In unclear situations, always verify the authenticity of the message directly with the sending organisation through another communication channel.
We have published a separate Information Security Now! (External link) article on scam messages sent in the name of child protection services (article in Finnish).
Traficom and Finnish Security and Intelligence Service: Cyber threat level remains elevated
Traficom and the Finnish Security and Intelligence Service (Supo) have issued a joint statement noting that the cybersecurity threat level in Finland remains elevated. The threat level increased in 2022 after Russia launched its large-scale attack against Ukraine.
Based on cases reported to the NCSC-FI at Traficom, Finnish organisations continue to be targeted by hostile cyber activity, and the number of serious data breaches and attempted intrusions has increased. The number of serious cases investigated by the NCSC-FI has more than doubled compared with the previous year. Findings of software vulnerabilities have also increased significantly, which greatly heightens the cyber threat to society. According to Supo, state-sponsored cyber activity against Finland remains active. Traficom and Supo nevertheless continue to consider the likelihood of cyberattacks capable of paralysing society on a broad scale to be low.
Attackers impersonate IT support in Teams calls
Scam attempts have been reported in which criminals call organisations via Microsoft Teams while impersonating IT support. The attacker may, for example, appear under the name “Help Desk” and claim that the user’s computer is experiencing problems. Under this pretext, the employee is instructed to install remote access software such as AnyDesk or Quick Assist, giving the attacker access to the victim’s device.
By default, Teams settings allow external contacts, which makes these scams easier to carry out. Organisations are advised to review and restrict their guest and external access settings, and to provide clear guidance to staff on how and through which channels IT support will actually contact them. Procedures for reporting suspicious contacts should also be reinforced among employees.
We have also published an Information Security Now! article on this topic, available here:
Malware distributed under the guise of PDF editing software
This week we also published an Information Security Now! article on a malware campaign in which criminals distribute malicious programmes disguised as PDF editing applications. The malware is spread, for example, through search engine advertisements or unreliable websites, and installing it can result in data theft or complete system compromise.
The safest way to avoid infection is always to download software from official app stores or directly from the manufacturer’s own website. Organisations should remind staff of safe software download procedures and prevent the installation of malicious programmes by managing workstation privileges.
Read the full Information Security Now! article here:
Malware review: Avalanche
The cyber criminal group Avalanche offers phishing and malware attacks to other criminals as a service. The group uses and spreads several malware families. The Avalanche data network maintains an infrastructure used by cyber criminals to conduct phishing and malware distribution campaigns, for example.
A system infected with malware related to Avalanche may be targeted by malicious activity that can include theft of user IDs and other kinds of sensitive information, such as banking or credit card information. Some types of malware can encrypt files and demand a ransom from the victim to allow them to access the files again. A malware infection may also enable remote access to the compromised computer, allowing it to be used for denial-of-service attacks or other criminal activities online.
Cyber criminals use the Avalanche botnet infrastructure to maintain or distribute different kinds of malware variants to victims. At least 40 major financial institutions have been targeted. Sensitive personal data of the victims may have been stolen, and the compromised systems may have been used in other malicious activities. The activities have included launching denial-of-service attacks or distributing malware variants to the victims’ devices, for instance. The Avalanche infrastructure has also been used in money laundering; people have been recruited to commit fraud by transporting and stealing money or merchandise.
Guidelines for preventing infection:
- Make sure that you install software and security updates and that your operating system is up to date.
- Check links that arrive via email or in a text message before clicking them; even if a link seems familiar, it may actually be a fraud. A better option is to go directly to the website with the browser or use a bookmark.
- Change passwords regularly; do not recycle passwords between services.
- Use antivirus software and keep it up to date.
Supo contributes to new international cybersecurity guidance
The US Cybersecurity and Infrastructure Security Agency (CISA), together with numerous international authorities, has published guidance on countering state-sponsored Chinese actors targeting critical infrastructure. From Finland, the Finnish Security and Intelligence Service (Supo) contributed to the work, reflecting Finland’s active role in the international cybersecurity community. The guidance provides practical advice for organisations’ technical specialists.
Further information is available via the links below:
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI.
- Instructions for victims of data leaks (External link)
Recognise online scams and protect yourself from them
Vulnerabilities
This week, we published a vulnerability advisory on a critical flaw affecting NetScaler ADC and NetScaler Gateway products.
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (reporting period 23–29 August 2025). The purpose of the weekly review is to share information about current cyber phenomena. The review is intended for everyone from cyber security professionals to ordinary people.