Information security now!
This week, we report on financial losses caused by child protection-themed scam messages, highlight Microsoft’s new authentication methods and present our weekly malware review. We also invite you to join the Critical code webinar.
Topics covered in this week’s review

- Financial losses caused by child protection-themed scam messages
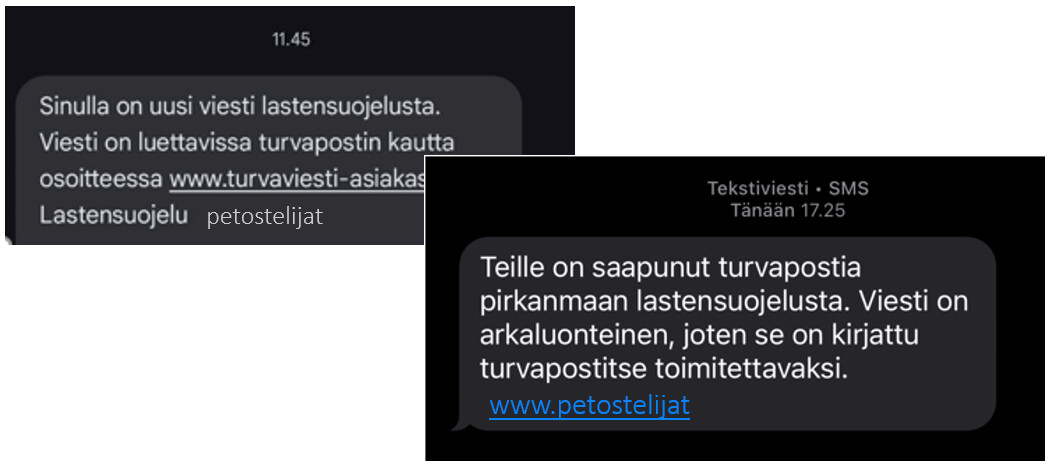
Criminals have been actively distributing scam text messages in which they pose as, for example, social workers and refer to child protection. Victims have included individual organisations, with financial losses ranging from several thousand euros to as much as one hundred thousand euros.
The software company Visma Solutions reported that some of its Netvisor customers have also fallen victim to phishing, after criminals gained access to their strong authentication credentials. The phishing messages were disguised, for example, as child protection notifications. To protect its customers, Netvisor has introduced an additional verification step for payments.
We have published a separate Information Security Now! (External link) article on scam messages sent in the name of child protection services (article in Finnish).
In the scam text messages distributed by criminals, they pose as social workers and refer to child protection.
Transition to Microsoft’s new authentication methods
Microsoft has announced that it will transition to new authentication methods in Entra ID by 30 September 2025. At that point, the legacy MFA (Multi-Factor Authentication) and SSPR (Self-Service Password Reset) policies will be retired. This change applies to all organisations, including Global Administrator accounts. Please ensure that your organisation has already enabled the new authentication methods in its Microsoft 365 subscription, or that plans for implementation are well under way.
Once the legacy MFA and SSPR policies are retired, users may lose the ability to sign in or reset their passwords if the new authentication methods are not in place. This applies to regular users as well as administrators. Importantly, Global Admin accounts may lose access to the Microsoft 365 environment if authentication methods have not been defined in the new Authentication Methods Policy settings.
What to do:
- Migrate to the new Authentication Methods Policy before 30 September 2025.
- Use the Migration Wizard to support a secure and gradual transition.
- The legacy settings will remain in effect during the transition, but will be fully retired after the deadline.
Critical code – webinar for higher education institutions, 9 September 2025
We have seen cautionary examples in Finland as well of what can happen when software security fails. The consequences can be serious, ranging from personal data leaks to disruptions in services critical to society. Software security is not just a technical matter; it is a key element of societal resilience and public trust—in short, security of supply.
You are warmly invited to a webinar on 9 September, from 9.00 to 11.00, where we will explore what kinds of skills are needed—now and in the future—to ensure the security of software systems.
Speakers include experts from the National Emergency Supply Agency, the NCSC-FI at Traficom and Solita.
Malware review: Mirai
Mirai is malware that infects smart devices and home routers. It creates a remotely controlled network of compromised smart devices, often referred to as a botnet or zombie network. These botnets are often used to launch distributed denial-of-service (DDoS) attacks. In late 2016, a Mirai botnet brought down large parts of the internet, significantly slowing many popular services and affecting millions of users.
Mirai scans the internet for IoT (Internet of Things) devices running on ARC processors. These devices can range from agricultural equipment, irrigation systems, surveillance cameras and cars to smart refrigerators. ARC processors use a stripped-down version of the Linux operating system. If the default username and password have not been changed, Mirai can log into the device and infect it.
The Mirai source code has also been developed into many other variants, including Okiru, Satori, Masuta and PureMasuta. IoTrooper and Reaper can also be traced back to Mirai. Reaper is capable of targeting a wide range of device developers and has far more advanced capabilities to control parts of its botnet.
How to protect yourself:
- Keep your device software up to date.
- Change default passwords.
- Restrict access (for example, avoid exposing devices directly to the internet, and use NAT on your home network – though for home users, this is often a paid service).
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI. (External link)
- Instructions for victims of data leaks (External link)
Learn how to detect and protect yourself against online scams
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (reporting period 28 August - 4 September 2025). The purpose of the weekly review is to share information about current cyber phenomena. The review is intended for everyone from cyber security professionals to ordinary people.