Information security now!
This week we discuss denial-of-service attacks and their impacts. We also discuss the Bulletproof Hosting phenomenon as an enabler of criminal activity. We briefly outline an exercise in which security authorities practised responding to state-sponsored cyber influence operations, and we also cover European Cybersecurity Month, the theme of which is improving your everyday cybersecurity skills. In this week's malware review, we introduce Locky.

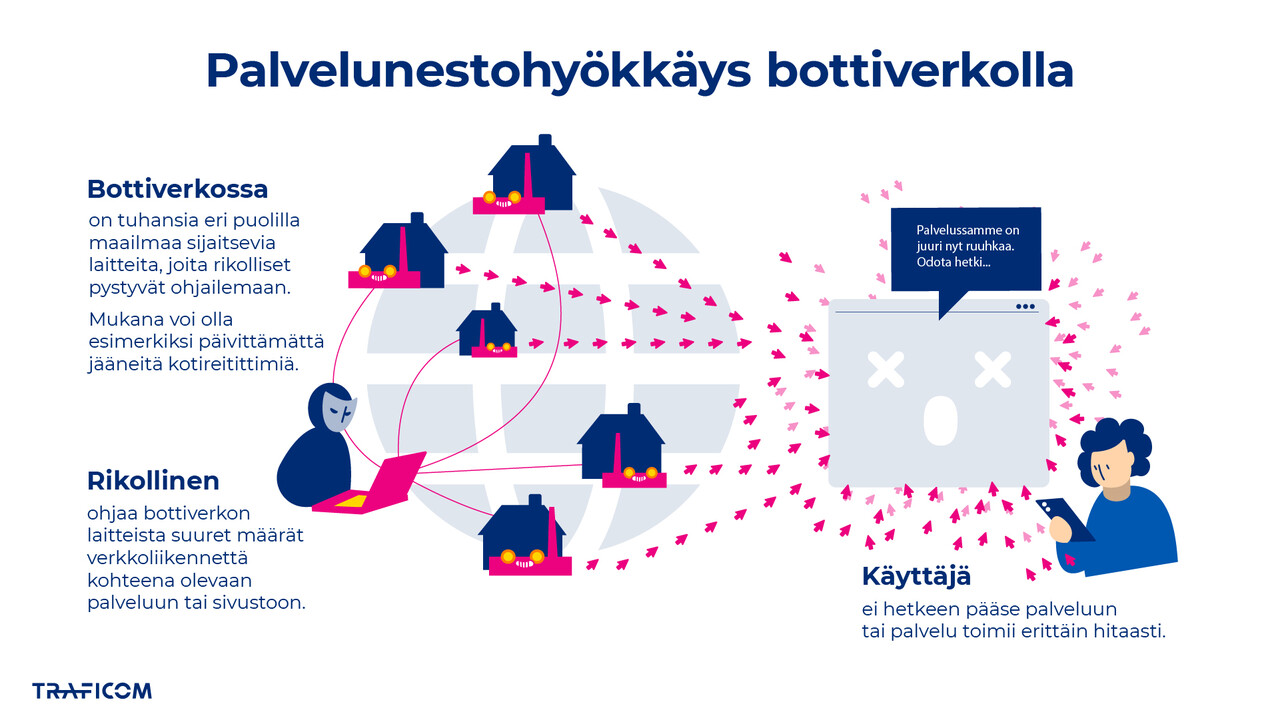
Denial-of-service attacks are part of everyday life online
A denial-of-service (DoS) or distributed denial-of-service (DDoS) attack is a common form of cyber attack, and its effects are quickly visible to users: websites may slow down or crash completely, disrupting everyday online activity. Such attacks are often carried out using a botnet that sends resource-intensive requests or floods the target with traffic until normal operations are disrupted. Although these attacks do not lead to data breaches, they can cause financial losses or reputational damage to the service provider.
Denial-of-service attacks are used, for example, in hacktivism as a show of cyber capability and as a message to an international audience. Their visibility makes them effective tools for influence. In some cases, attackers also seek financial gain by demanding payment to stop the attack.
In Finland, large-scale and prolonged disruptions are rare because organisations invest heavily in protecting their services. However, attackers’ methods continue to evolve, which is why protection practices should be reviewed regularly. Key elements include preparedness exercises, system updates, monitoring and open communication. When procedures are planned and tested in advance, the impact of an attack can be minimised and recovery accelerated.
Individual users can also help. Keeping devices up to date, changing default passwords and using strong credentials can prevent one’s own device from becoming part of a botnet. In this way, everyone can contribute to reducing the power of denial-of-service attacks.
Denial-of-service attacks are part of everyday life on the internet, but with the right preparedness measures, their effects can be managed.
We have published an Information Security Now! (External link) article on the topic: Anticipation is the best defence against denial-of-service attacks (in Finnish) (External link)
Bulletproof hosting is a major enabler of criminal activity
The term bulletproof hosting (BPH) refers to service providers who offer online services to criminals or other malicious actors in a way that makes it difficult for authorities to intervene. Such providers do not take active measures against their users’ criminal activities, such as distributing malware, sending spam or hosting fraudulent websites.
These providers often operate in regions where law enforcement authorities have limited interest in, or resources for, investigating such activities. In addition, BPH providers use complex technical arrangements to make takedown and abuse requests difficult to implement.
Criminal activity relying on bulletproof hosting services has become more difficult as global cooperation between authorities and the private sector continues to tackle the problem. Shutting down these services imposes costs on criminals, as they must rebuild infrastructure to replace that which has been exposed or taken down.
At the NCSC-FI, work is currently under way to develop, for example, a blocking request process related to malicious online traffic and activity. The aim is to respond more effectively to BPH operations, for instance by taking down harmful .fi domains and providing filtering recommendations to internet service providers.
Raising awareness of BPH activity is important not only for service providers but also for companies using online platforms. Some providers operate in a grey area, seeking to attract ordinary businesses as customers. Their clients may end up indirectly funding criminal activity, and if the provider becomes subject to sanctions or a shutdown, this represents a significant business risk for the company.
We have published an Information Security Now! (External link) article on the topic: (External link) Bulletproof Hosting – a major enabler of criminal activity (in Finnish) (External link)
Security authorities trained to respond to state-sponsored cyber influence
Nearly 200 experts from various security authorities took part in the national KYHA cybersecurity exercise, held at JAMK University of Applied Sciences in Jyväskylä from 22 to 26 September 2025. This year’s theme focused on responding to state-sponsored cyber influence. The main goal of the exercise was to strengthen authorities’ capabilities to prepare for and respond to attacks by actors with extensive resources.
The NCSC-FI participates in national cyber exercises annually to practise its own operations. At the same time, it supports other organisations’ exercises by receiving incident reports, assisting in their resolution, and sharing threat intelligence and situational awareness with different stakeholders.
Given the global security situation, cyber exercises are more important than ever. Continuous training helps maintain expertise, upholds a high level of cybersecurity in society, and develops organisations’ and society’s ability to recover from serious disruptions. Exercises also allow organisations to test their processes and operational models, while practising crisis communication plays a key role.
The national cyber exercises are organised by JYVSECTEC (Jyväskylä Security Technology), a research, development and training centre located at JAMK’s IT Institute, in cooperation with the Ministry of Transport and Communications. The Security Committee also takes part in the exercises in an advisory role.
- Improving everyday cybersecurity skills as the theme of European Cybersecurity Month
October marks the 13th European Cybersecurity Month (ECSM). The campaign aims to raise awareness of cybersecurity among citizens and organisations, share good practices, and provide up-to-date information on safe online behaviour. This year’s focus is on everyday choices that affect both our own and others’ safety online.
Cybersecurity is not just a technical issue — our daily choices and habits influence how safe the online environment is for all of us. There are many ways to learn about safe internet use, for example through games or online courses. The social media and online fraud prevention network, coordinated by the Finnish Transport and Communications Agency Traficom’s NCSC-FI, is campaigning for a safer online experience together with Aalto University’s SecPort website. The site offers practical tips and learning materials to help citizens strengthen their cybersecurity skills.
- Weekly malware review: Locky
Locky is a ransomware strain that spread widely in 2016. It encrypts the files on an infected computer and demands a ransom for their recovery. It spread primarily through email attachments, often appearing as harmless invoices or documents containing macros. When a user opened the file and allowed macros to run, the malware activated, downloaded the encryption component, and began encrypting files.
Locky encrypted a wide variety of file types, making its effects severe for both individual users and organisations. The encryption used strong algorithms, and without paying the ransom, there was realistically no way to recover the data. Locky also used complex techniques to avoid detection and changed file extensions, making it harder to identify the affected files.
The impacts were extensive: many companies and hospitals were forced to pay ransoms or lost valuable data. Locky served as a model for many later ransomware variants, and its methods are still used in newer threats.
Protective measures:
- Do not open attachments or links from unknown sources.
- Keep your operating system and software up to date.
- Use up-to-date antivirus software and a firewall.
- Make regular backups of important files and store them offline.
Train users to recognise suspicious emails and attachments.
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
What to do if you get scammed
- Immediately contact your bank if you have made a payment based on a Learn how to detect and protect yourself against online scamsscam or a criminal has gained access to your online banking service or payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI. (External link)
- Instructions for victims of data leaks (External link)
- The most common types of online scams (in Finnish) (External link)
- Advice to help you protect your accounts (External link)
CVE: CVE-2025-20363
CVSS: 9
What: Cisco has released patches for 14 critical vulnerabilities affecting various products in the IOS product family.
Product: Cisco IOS and IOS XE
Fix: Update vulnerable products according to the manufacturer's instructions
Vulnerabilities in Cisco IOS and IOS XE devices (in Finnish) (External link)
About the weekly review
This is the weekly review of the National Cyber Security Centre Finland (reporting period 26 September–2 October 2025). The purpose of the weekly review is to share information about current cyber phenomena. The review is intended for everyone from cybersecurity professionals to ordinary people.