Your modem or router is the gateway to your home network, which is why it is especially important to keep it secure. Your modem and router may be two separate devices, or you may have a single device that serves as both a modem and a router. In these instructions, we go over the basics of router security to help you protect your home network and personal data.
This page details the most important security settings of your home network device that you should be aware of:
- Disable remote access to your router from outside your own network or make sure that the feature is secure.
- Change your default password.
- Updating your device – enable automatic updates.
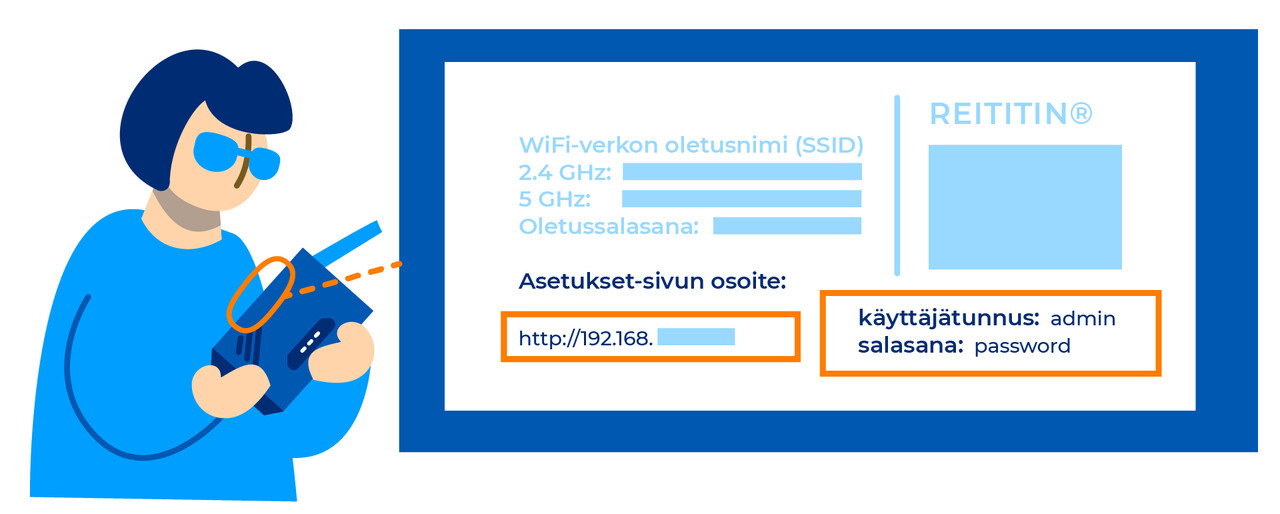
You can configure your home router via its admin portal, which you can access by entering your router’s IP address into your browser address bar on your computer or laptop and signing in using the username and password marked on your router. Depending on your router’s settings, signing in to the admin portal may require your computer or laptop to be connected to the router’s network. You can find the IP address used for configuring your router in the device’s user manual or on a sticker attached to the device, for example. The password is marked on the router, unless you have already changed it.
Why would criminals be interested in my device or home network?
Criminals are constantly scouring the internet for vulnerable network devices both manually and by automated means. Once hijacked, network devices can be used to carry denial-of-service attacks, for example. Distributed denial-of-service (DDoS) attacks are often carried out using remote-controlled devices that the attacker has hijacked. Criminals can also use hijacked network devices to cover their own tracks or carry out attacks from IP addresses in the target country. The latter is effective because malicious traffic originating from the network of a domestic ISP is not as easy to detect as malicious traffic originating from a foreign network. Denial-of-service attacks are also often prevented by temporarily cutting off traffic originating from foreign networks. Such measures will obviously not affect domestic hijacked devices. This is a good example of why a single hijacked device in the domestic network will not always be immediately detected based on the various rules used in data traffic management.