Information security now!
This week we cover the ongoing wave of M365 account compromises, the exploitation of invoicing services in invoice fraud, the opening of a new EU cybersecurity funding call and the opportunity to comment on the EU Cyber Resilience Act. This week’s malware review focuses on the Nymaim trojan.
Topics covered in this week’s review
- Microsoft 365 accounts are still being compromised at a record rate –- read the guidance and prevent data breaches in your organisation
- Criminals impersonate invoice senders – check before you pay
- New call for proposals under the Digital Europe Programme: EUR 50 million for cybersecurity
- Consultation on the conditions for delaying the reporting of actively exploited vulnerabilities or incidents under the Cyber Resilience Act (CRA) – have your say now!
- Weekly malware review: Nymaim

Microsoft 365 accounts are still being compromised at a record rate –- read the guidance and prevent data breaches in your organisation
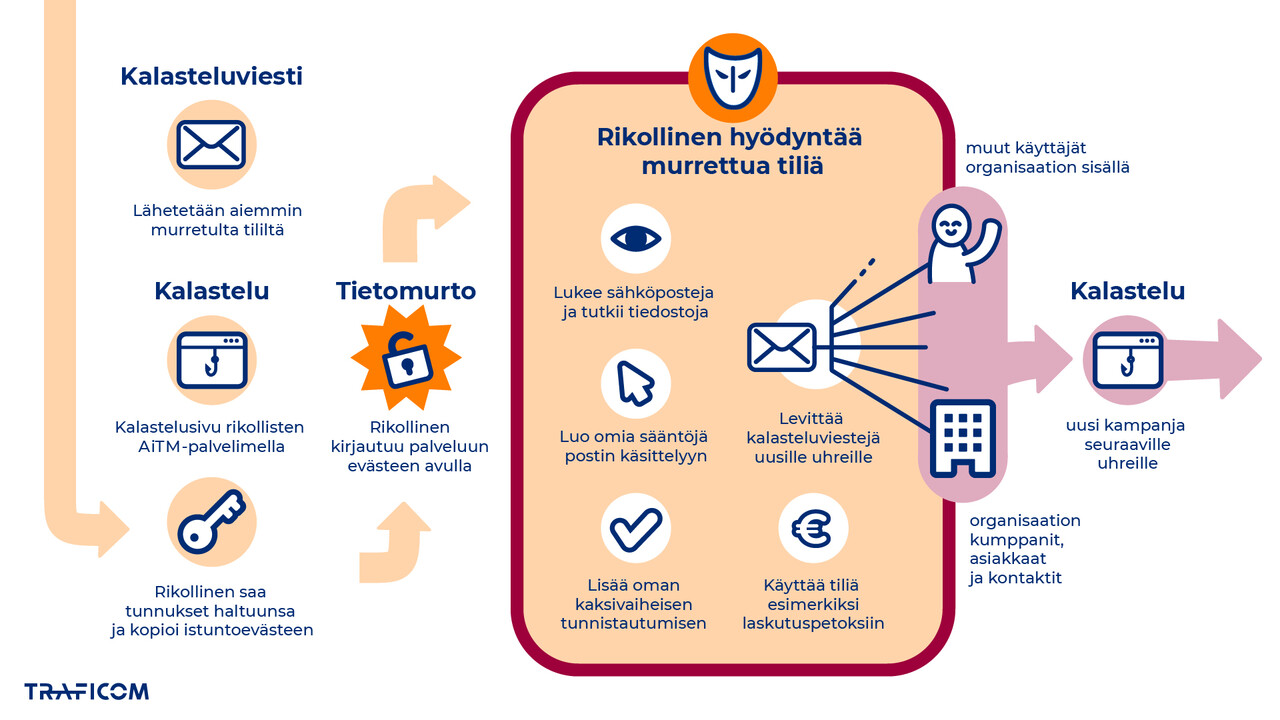
The NCSC-FI has received reports of Microsoft 365 account compromises at an increasing rate. We issued a severe alert about this already in September, due to the exceptionally high number of reports related to M365 account breaches or attempted breaches in August. Despite the alert, 117 cases were reported in September and 120 in October. The alert applies to all companies and organisations that use an M365 environment, as well as their employees and users.
Criminals log in to M365 services using stolen credentials, and compromised accounts are used to send new phishing messages and to carry out invoice fraud, for example. Account compromises enable unauthorised access to emails and documents, which exposes confidential information to misuse. At worst, account compromises can disrupt business, damage reputation and act as a gateway to wider attacks. Scam messages are often disguised to look like a contract or an invoice that requires the recipient to take action. The message may contain a link to a file that requires login credentials for the M365 service to open. Scam messages may be genuine file-sharing messages sent via a file-sharing service such as SharePoint or OneDrive, but the file shared on that service redirects the victim to a phishing site controlled by criminals. The appearance of authenticity can make scam messages particularly difficult to recognise.
User: Be very cautious—even with messages from known senders!
What makes the ongoing phishing campaign particularly deceptive is that the phishing messages often come from a familiar sender's compromised account. If you doubt the authenticity of the message you received, do not reply to it and do not click the links in it. Verify the message's authenticity by other means, for example by calling or using instant messaging. Also report a suspicious message to your organisation's IT support. Exercise caution when using M365 credentials. Always ensure that you are logging in to the genuine service before entering your login credentials.
M365 administrator: Review the NCSC-FI guidance to protect your organisation!
Organisations should implement multi-factor authentication (MFA) and also become familiar with other security measures in the M365 environment. You can enhance security with passwordless login methods and conditional access policies, for example. You can also block logins from specific countries or IP addresses, effectively limiting access to the countries where your users are expected to sign in to the M365 environment.
More information
Criminals impersonate invoice senders – check before you pay
In recent weeks, the NCSC-FI has received several reports of attempted invoice fraud targeting organisations. Criminals have managed to slip fraudulent invoices to organisations via various invoicing services, even directly into online banking services. These scams look credible because they use real companies' details, such as business IDs, and invoices are sent via the same services that are normally used.
The scam has been facilitated by criminals being able to register as a biller with various services. In recent invoice scams, for example, the business ID of Proton Lighting Suomi Oy has been used, as well as other variations that contain the word “Proton”, such as Proton Solutions Oy. Additionally, criminals have used Proton-themed email addresses in the details of fraudulent invoices, such as “asiakaspalvelu[.]proton@protonmail[.]com”.
In these scams, criminals exploit customers' trust in billing services, because the messages appear to come from genuine systems. Under the new EU Instant Payments Regulation, payment systems may warn that the system has been unable to verify that the payee's name and the account holder's name match. Scammers have instructed victims to ignore these warnings, even though the warnings have been legitimate.
The NCSC-FI recommends always verifying the authenticity of payment requests and unusual messages before making payments. Follow your organisation's payment procedures and do not skip any stage of the process. Organisations should establish and test internal procedures to ensure the accuracy of invoices.
If you suspect fraud or have received a fraudulent invoice, report it to the police and, if you wish, also to the NCSC-FI. If money has already been transferred, contact your bank immediately and report the matter to the police – prompt action can prevent losses.
New call for proposals under the Digital Europe Programme: EUR 50 million for cybersecurity
The second call for proposals for 2025 under the EU's Digital Europe Programme is now open. Through the programme, EUR 50 million in funding is allocated to cyber-related activities.
The Digital Europe funding programme supports the deployment of cyber secure solutions and the use of previous research results. In the second application round, four different calls are open for cybersecure tools and services relying on AI, for the uptake of innovative cybersecurity solutions for SMEs, for coordinated preparedness testing and for the cybersecurity of submarine cables. The calls open on 28 October 2025 and the submission period runs until 31 March 2026.
The National Coordination Centre (NCC-FI) at the NCSC-FI offers free support and advice, such as guidance on selecting suitable calls and support in finding partners.
Find out more about the NCC-FI's services here (External link)or contact the centre by email: ncc-fi@traficom.fi .
Consultation on the conditions for delaying the reporting of actively exploited vulnerabilities or incidents under the Cyber Resilience Act (CRA) – have your say now!
Under the EU Cyber Resilience Act (CRA), manufacturers of products with digital elements must notify the authorities of any actively exploited vulnerabilities or incidents affecting information security.
Notifications are submitted to the national Computer Security Incident Response Team (CSIRT), which may in exceptional circumstances delay sharing the information with counterpart authorities in other EU Member States.
The European Commission is now seeking feedback on the proposed delay conditions. Comments can be submitted on the Better Regulation portal until 13 November 2025 via the link below.
Weekly malware review: Nymaim
Nymaim is a "Trojan downloader", i.e. malware that downloads and executes other malware on compromised systems. This malware has often been used to install ransomware. Nymaim displays a personalised lock screen while it downloads another piece of malware. Nymaim typically spreads through malicious email attachments, compromised websites or fake software updates.
Nymaim is distributed via exploit kits or files. Usually, the names of malicious files relate to popular search terms that people use when searching for applications. Nymaim may appear on a computer as pop-up adverts, for example. The operating system may also slow down significantly and the web browser may show an unusual number of adverts. Showing adverts is one way malware makes money.
How to protect yourself from the Nymaim malware:
- Carefully consider where you download apps from and whether downloading is secure. Malware can spread through freeware.
- Do not click carelessly. Links in emails can be used to distribute malicious content.
- Think twice before downloading email attachments.
- Think carefully about what and where you download, install and run on your device.
- Make sure the operating system and applications have received the latest updates.
- Keep your antivirus software enabled and up to date.
An antivirus program usually removes the malware or at least reports that it has taken action..
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
About the weekly review
This is the weekly review of the National Cyber Security Centre Finland (reporting period 24–30 October 2025). The purpose of the weekly review is to share information about current cyber phenomena. The review is intended for everyone from cybersecurity professionals to ordinary people.