Information security now!
This week, we report on the widespread impact of M365 account breaches observed in September and share guidance on how to protect against them. We also cover a large-scale data breach that occurred in Sweden and examine recent supply chain attacks. In addition, we provide information on the upcoming reporting obligation for vulnerabilities under the Cyber Resilience Act, which enters into force on 11 September 2026. We explain what organisations need to do to comply. In this week’s malware update, we take a closer look at the Tinba banking trojan.
Topics covered in this week’s review
- Surge in Microsoft 365 account breaches continues in September – adopt protective practices now
- Data breach in Sweden exposes personal details of around one million individuals
- What are supply chain attacks?
- Reporting obligation for vulnerabilities and serious security incidents under the Cyber Resilience Act will take effect on 11 September 2026
- Malware review: Tinba

Surge in Microsoft 365 account breaches continues in September – adopt protective practices now
By the end of August 2025, the NCSC-FI had received a total of 330 reports related to Microsoft 365 account breaches or attempted breaches. A record-breaking 70 cases were reported during August alone. However, the accelerating trend has continued into September, and it now seems likely that August’s record will be surpassed. In the first three weeks of September, 57 new cases had already been reported. Numerous organisations have been exposed to breaches and subsequent phishing emails, and several account compromises may occur within the same organisation.
On 9 September 2025, the NCSC-FI issued a severe alert regarding M365 account breaches. The alert targets companies and other organisations, as well as their employees who use M365 products. Criminals use stolen credentials to access M365 services, and compromised accounts are then exploited to send new phishing messages and to commit invoice fraud. Account breaches enable unauthorised access to emails and documents, exposing confidential data to misuse. At worst, such breaches can lead to business disruptions, reputational damage, and serve as a gateway to broader attacks. They may also cause significant financial losses.
We have also published an Information Security Now! article on the topic: “Protect your Microsoft 365 environment in advance – access to a user account can still be blocked even after credentials have been leaked.” The article explains how Conditional Access policies can help organisations prevent Microsoft 365 breaches—even in cases where an attacker has obtained a user’s credentials. The article is especially intended for administrators of organisations using M365 services.
Data breach in Sweden exposes personal details of around one million individuals
A data breach targeting the Swedish organisation Miljödata has sparked concern in Sweden and also received attention in Finland. The NCSC-FI’s information security specialist Roni Kokkola also commented on the matter to MTV News (https://www.mtvuutiset.fi/artikkeli/kyberturvallisuuskeskus-ruotsin-tietomurrosta-ei-voida-sulkea-pois-ettei-vastaavia-tapauksia-ilmenisi-myos-suomessa/9222280 (External link)).
According to public information, the data breach affects more than one million people (https://yle.fi/a/74-20182802 (External link)). Miljödata is an organisation that provides human resources management systems to the municipal sector in Sweden. The data leaked in the breach includes, among other things, personal data and employee IDs.
According to the most recent information, company data has also been leaked in the breach (https://yle.fi/a/74-20183096 (External link)).
Data breaches of this scale are rare in the Nordic countries. A great deal of public information is available about the 2024 data breach targeting the City of Helsinki. The NCSC-FI has communicated on the topic and on the related report by the Finnish Safety Investigation Authority (SAIF) in Weekly Review 25/2025 (https://kyberturvallisuuskeskus.fi/en/news/weekly-review-national-cyber-security-centre-finland-ncsc-fi-252025 (External link)).
The Helsinki data breach was discussed, for example, in the Digital and Population Data Services Agency’s (DVV) VAHTI current affairs briefing on 20 August, which can be viewed as a recording here (External link).
The summer highlights from the Helsinki data breach remain relevant for every organisation in preparing for cyberattacks:
- Know what devices and products are in use in your organisation, especially at the network edge
- Update devices regularly and replace outdated equipment in time
- Ensure that edge devices use multi-factor authentication or another secure method of access control
- Monitor the environment, at least for critical devices
- Practise regularly so that critical events are detected early and handled appropriately
What are supply chain attacks?
A supply chain attack is a type of cyberattack in which criminals do not strike directly at the final target but instead exploit a supplier, subcontractor or software partner to gain access to the target organisation. Once access to the actual target has been secured, it can be used for various further attacks, such as data breaches and ransomware attacks.
Attacks on supply chains can affect several organisations at once. Recent examples of such attacks include infections with the BadBox 2.0 malware as well as the incidents reported in recent weeks involving npm packages in the Node.js ecosystem. In addition, the Valio data breach case at the end of 2024 demonstrates how weaknesses in service providers or outsourced systems can lead to serious consequences for both the victims of data leaks and the organisations themselves.
The importance of supply chains in cyber security is constantly increasing, as organisations are relying more and more on external suppliers and software partners. Good asset management helps in identifying and managing supply chain risk. As part of the asset register, organisations should also compile a list of actors, bringing together service providers and suppliers as well as the products they deliver.
Protecting against this threat also requires comprehensive risk management: evaluating suppliers, continuous monitoring, software checks and strict contractual obligations. In addition, organisations need to build cooperation across different parts of the supply chain, since cyber security is not only the responsibility of an individual actor but of the entire network. Preventing attacks requires both technical solutions and a collaborative approach.
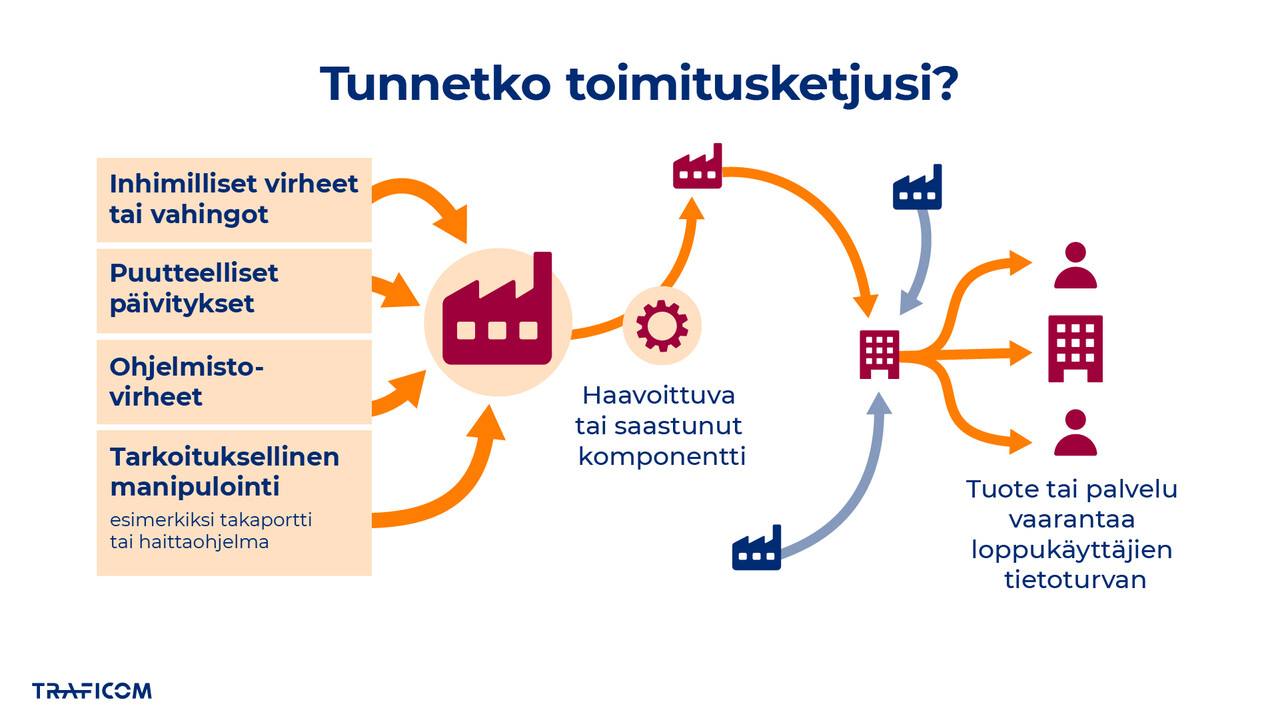
Read more:
Reporting obligation for vulnerabilities and serious security incidents under the Cyber Resilience Act will take effect on 11 September 2026
The EU’s Cyber Resilience Act (CRA) introduces new obligations for reporting actively exploited vulnerabilities and severe incidents affecting the security of products.
The CRA applies to products and software with digital elements that are directly or indirectly connectable to another device or network. The reporting requirements for vulnerabilities cover all relevant products on the EU market, not only those being newly placed on the market.
What should manufacturers and importers do now?
- Check whether the product falls within the scope of the CRA. If it does, also identify in which EU Member States the product has been made available.
- Update vulnerability management processes to meet CRA requirements: How will you act when you receive a vulnerability notification? How will you submit a notification yourself? Take CRA deadlines into account.
- Train staff: Ensure that product development, information security and legal teams are familiar with the CRA requirements.
- Follow the NCSC-FI’s communications on the CRA and contact the NCSC-FI if necessary.

Malware review: Tinba
Tinba is a type of malware that attempts to infect a terminal device and gain access to the user’s online bank or other accounts that contain funds to steal the user’s money. The trojan called Tinba or Tiny Banker is focused on attacks against online banks especially in Russia. Tinba is one of the smallest known trojans. Tinba’s source code has been published online, and new variants of the malware appear regularly.
In a system infected by Tinba, the browser may behave abnormally or the system may crash. Typically, an unexpected pop-up window is shown on a bank’s website with a request to do something out of the ordinary, such as enter the user’s sensitive information in the pop-up. Bank trojans are a sophisticated type of malware; they wait and hide in the infected system until the user attempts to log in to an online bank. Tinba uses a keylogger to steal the username and password of the account and sends them to criminals.
Tinba typically infects a device through downloads of free software, infected links in phishing messages or attachments. Tinba can also spread if the user clicks a pop-up window or downloads content from the dark web or torrent files.
How to protect yourself:
- Do not click email links without checking them first, and do not execute files or download attachments without considering their purpose or if they are necessary.
- Be cautious with any unusual request or content received by email and never send your sensitive personal data carelessly by email.
- Monitor whether you receive unusual messages, pop-ups or requests when logging in to online banking or other financial services.
- Check the appearance and address of a website for changes if the site raises suspicion.
- Download mobile applications only from trusted sources, and never from outside the official app store.
- Ensure that backups exist and are up to date, as banking trojans can also spread ransomware.
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
WHAT TO DO IF YOU GET SCAMMED
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or payment card information.
- File a police report. You can file a police report online. (External link)
- You can also report the incident to the NCSC-FI.
- Instructions for victims of data leaks (External link)
Recognise online scams and protect yourself from them
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (reporting period 13–19 September 2025). The purpose of the weekly review is to share information about current cyber phenomena. The review is intended for everyone from cyber security professionals to ordinary people.