Information security now!
This week, we take a look at the most common ways attackers have recently been trying to deceive ordinary citizens. Their main targets are money and information. The range of scams and phishing messages is broad, so everyone should remain alert and examine new messages carefully. This week also saw the Cyber Security Nordic fair take place, where the NCSC-FI was present as well.

The most common recent ways to deceive citizens
Criminals are becoming increasingly cunning in their efforts to steal information and money from ordinary citizens online. Various types of scams now reach victims through multiple platforms and applications, and their quality improves year by year. As technology advances, producing fluent Finnish text has become easier than ever. For example, with the help of artificial intelligence, it is easy for criminals to refine the language of a translated message to make it sound more convincing for use in scams.
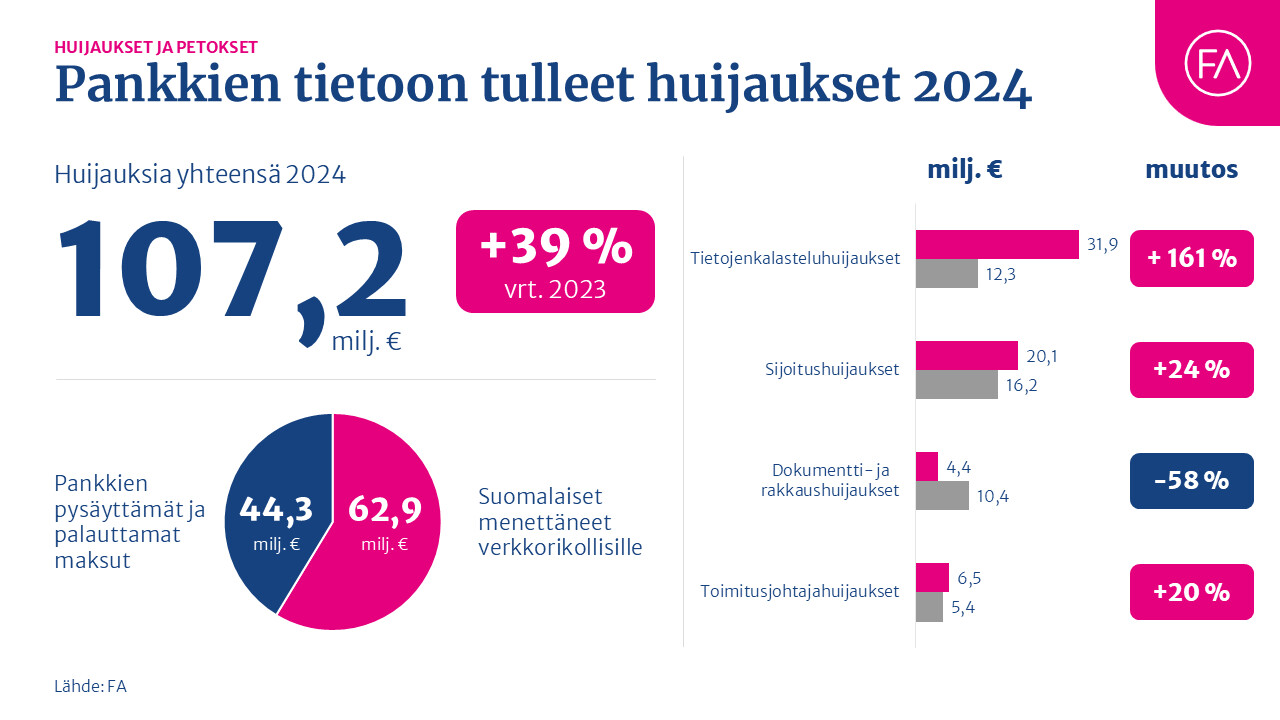
According to Finance Finland, Finns lost EUR 62.9 million to fraudsters last year. The real figure is likely even higher, as not all financial losses are reported to the police or banks. It is also important to note that cooperation between banks, telecommunications operators and authorities prevents an enormous amount of financial losses every year. In 2024, banks prevented losses totalling EUR 44.3 million through their actions.
 (External link)
(External link)Read more:
Every week, the NCSC-FI detects and receives a vast number of different phishing messages. In most cases, these lead to a phishing website where the scammer attempts to trick an ordinary user into entering their online banking credentials. For organisations, the most serious problem related to phishing messages has been data breaches caused by M365 credential phishing, which we reported on most recently last week (External link).
Scam calls and messages in the name of the NCSC-FI
This autumn, Traficom has become aware of cases in which criminals have called victims while posing as experts from the NCSC-FI (External link). In these scam calls, the criminals have claimed, among other things, that the victims’ mobile phones are infected with viruses and that NCSC-FI experts will come to collect the devices. The callers have also asked for online banking credentials and payment card details. Criminals have additionally sent WhatsApp messages themed around the EU’s NIS 2 cybersecurity directive, referring to an alleged information security notification made by the recipient’s organisation. Traficom published a news release about the most recent bank phishing messages on its website on 6 November 2025 (External link).
Impersonation of authorities is common
Criminals leave no stone unturned when it comes to choosing phishing themes. This autumn, they have actively spread (External link) fraudulent text messages in which they impersonated, for example, social workers or police officers, and referred to child protection matters. Victims have included individual organisations, and during autumn 2025, financial losses have ranged from several thousand euros to as much as one hundred thousand euros. Similar activity has also been observed in November, and reports of financial losses have been submitted to the NCSC-FI in recent days.
Use of popular platforms in scams
Criminals moved to social media platforms some time ago to target ordinary people. Recently, the NCSC-FI has received increasing numbers of reports of various scam attempts on platforms such as Teams and instant messaging services like WhatsApp. Scam attempts have also arrived via work phones and email.
We published an article earlier in the autumn about scams on the Teams platform (External link) (in Finnish).
Criminals also impersonate organisations
In the autumn, several scam attempts have been detected in which criminals impersonated pension companies (External link). In these scams, customers were lured into clicking on links and entering personal or banking details on fake websites. Such messages may arrive by email or text message, and their appearance often closely resembles genuine communications from pension companies.
The fraudulent messages claimed, for example, that pension payments have been suspended or that the recipient must update their details via the link to continue receiving payments. In reality, the link led to a phishing website.
Extortion email campaigns appear at regular intervals
Different types of extortion emails are sent out every year under various themes. During the summer (External link), the NCSC-FI received numerous reports of extortion messages in which a scammer claimed to have gained access to the victim’s devices and secretly recorded them while visiting adult websites. The message proposed an “agreement” and attempted to extort money from the victim by demanding payment to a specified Bitcoin address. The messages were written in Finnish, and the sender address was spoofed so that the message appeared to come from the recipient’s own email account. Similar campaigns are expected to reappear in future waves of emails.
These messages are fraudulent, and the demanded sums of money should never be paid. The message should simply be ignored and deleted.
Weekly reports of CEO fraud
During the autumn, the NCSC-FI has received several reports of CEO fraud. Criminals use social engineering, weak internal processes and current events to gain financial benefit. They typically request urgent bank transfers, gift card purchases or payments of falsified invoices. These scams particularly target organisations. You can read more in our article here (External link).
Cryptocurrency investments attract scammers
Cryptocurrency investment services have also recently attracted the attention of scammers. Significant amounts of money are tied up in various cryptocurrencies, which criminals try to obtain through scams. Users of crypto investment services have had their accounts hacked and large sums of money stolen.
Scammers have been sending messages that have been faked to look like official maintenance messages. The scam messages claim that the victim's account is being exploited, or an attempt is being made to hack into or disable the multi-factor authentication that is linked to the account. For example: “We have received a request to unbind your 2FA. If this wasn’t you, call this number.” As with scams in general, the scammer tries to create a sense of urgency and scare the victim into being careless.
Common manipulation techniques used by criminals – and how to defend against them
- Fear-based manipulation: Scam messages may threaten with account closure, freezing or, for example, being suspected of a crime.
- Exploiting sympathy: Scammers claim there is an emergency and ask for money. Do not transfer money until you are sure who is asking and why.
- Appealing to authority: The messages may appear to come from authorities. At first glance, the sender’s information may appear legitimate.
- Too good to be true: Messages about winning a prize or receiving free gift cards may be scams. Ask yourself if you even entered the prize draw.
- Building trust: Long-term scams, such as romance or investment fraud, are based on building trust before asking for money. Be cautious when someone asks you for money.
- Remember: stop and think—what is the sender’s motive, and why is the message urgent or threatening? Verify the authenticity of the message through official sources. If you are asked for money, try to verify who is asking and whether the message is genuine.

How do we protect the digital society? InfoSec 2025 seminar at Cyber Security Nordic
The Finnish InfoSec 2025 seminar brought together cybersecurity experts and authorities at the Helsinki Expo and Convention Centre on 5 November as part of the Cyber Security Nordic event. Organised by Traficom and the National Emergency Supply Agency (NESA), the event explored how to safeguard a society that is becoming increasingly dependent on digital infrastructure.
In his opening remarks, Traficom’s Director-General Jarkko Saarimäki highlighted the role of public authorities as enablers of a sustainable, smooth and secure digital everyday life. The NCSC-FI supports this mission by providing up-to-date situational information on threats and preparedness. “Cooperation between authorities, the private sector and citizens is Finland’s strength in countering cyber threats,” Saarimäki noted.
The NCSC-FI’s Director-General Anssi Kärkkäinen gave an overview of the past year, emphasising that the level of cyber threats has remained high. The NCSC-FI has had to handle an increasing number of serious and critical cases. Finland’s strength lies in proactive preparedness, but maintaining constant vigilance remains essential. Key factors include cooperation, protection of critical infrastructure, identification of dependencies, and diverse training and exercises.
The keynote speaker of the seminar was Deputy Head of Division Viktor Vorobei from the State Special Communications Service and Information Protection of Ukraine, who shared experiences of cybersecurity in Ukraine during the war. He identified limited resources, trust and information sharing, and an outdated regulatory framework as key challenges. As solutions, Vorobei highlighted raising awareness, improving communication between authorities and users, and developing competence.
In a panel discussion, international experts considered what protecting critical infrastructure means in practice and what technology, cooperation and preparedness it will require in the future. The discussion was moderated by Baiba Kaskina, General Manager of the National Cyber Security Centre of Latvia.

Suvi Lampila from SSH Communications Security spoke about quantum-safe algorithms, while Mikko Alasaarela from Agion discussed AI agents. Karoliina Kemppainen, Chief Specialist at the NCSC-FI, addressed the critical importance of secure code in cybersecurity-focused software development, emphasising that this concerns everyone: even if a company does not develop software itself, it still acquires and uses it.
Finally, Juha Ilkka, Chief Preparedness Specialist at the National Emergency Supply Agency, summarised the day’s discussions and invited participants to next year’s seminar in October 2026.
Malware review: Ngioweb
Ngioweb is a Linux-based malware that exploits vulnerable IoT and SOHO routers and other devices to incorporate them into a botnet. This enables, among other things, the relaying of malicious traffic through the infected device, the launching of denial-of-service attacks and the theft of data stored on the device.
Ngioweb uses automated loader networks and scripts designed to find exploitable devices. Some versions of the malware operate primarily in memory, which makes detection and recovery difficult. Infected devices have been observed widely across multiple countries and are commonly used to provide commercial and criminal proxy services.
How to protect against Ngioweb-type threats:
- Keep routers and IoT devices up to date with the latest firmware.
- Change default device passwords and use strong, unique passwords or key-based authentication.
- Disable remote management unless it is strictly necessary and restrict administrative access to trusted networks only.
- Block unnecessary ports and suspicious C2 connections.
- Maintain an inventory of devices on your network and decommission obsolete or unused devices.
- If you suspect a malware infection, perform a factory reset, update the device immediately and change passwords. Also consider replacing the device if the vendor no longer provides updates.
Recently reported scams
In this summary, we provide information about scams reported to the NCSC-FI during the past week.
What to do if you get scammed
- Immediately contact your bank if you have made a payment based on a scam or a criminal has gained access to your online banking service or payment card information.
- File a police report. You can file a police report online. (External link) (External link)
- You can also report the incident to the NCSC-FI. (External link) (External link)
- Instructions for victims of data leaks (External link) (External link)
Learn how to detect and protect yourself against online scams
Tutustu Viikkokatsaukseen
This is the weekly review of the National Cyber Security Centre Finland (reporting period 31 October - 6 November 2025. The purpose of the weekly review is to share information about current cyber phenomena. The review is intended for everyone from cyber security professionals to ordinary people.