Information security now!
Recently, criminals have started to register scam websites in Finland’s national .fi domain as well. The aim of these websites has been to exploit the good reputation of the .fi domain to phish for people’s bank credentials.
Topics covered in this week’s review
- Phishing websites in the .fi domain: why are the authorities not doing anything – or are they?
- Multi-factor authentication protects user accounts, but is no substitute for user vigilance
- Back to school! Staying safe on the digital school path
- Vulnerabilities made for rainy Cyber Weather in July
Phishing websites in the .fi domain: why are the authorities not doing anything – or are they?
A relatively new phenomenon emerging in recent weeks has been phishing websites that use Finland’s national domain name extension .fi, which have been used to phish for OP Group bank credentials. These websites have been all but impossible to tell apart from real login pages on the basis of their content alone, and links to the phishing sites have been widely distributed via email.
The scam websites discovered so far have used addresses that can be identified as fraudulent on the basis of ending in “-op.fi”, such as "turvallisuusNNN-op.fi" or “petospalveluNNN-op.fi”, with NNN being a sequence of numbers. The use of the hyphen in the domain names is particularly noteworthy, as the real address of OP’s online bank ends in "op.fi". The hyphen makes all the difference, as illustrated by this second example: the imaginary address "turvallisuus-traficom.fi" would be completely different from “turvallisuus.traficom.fi”.
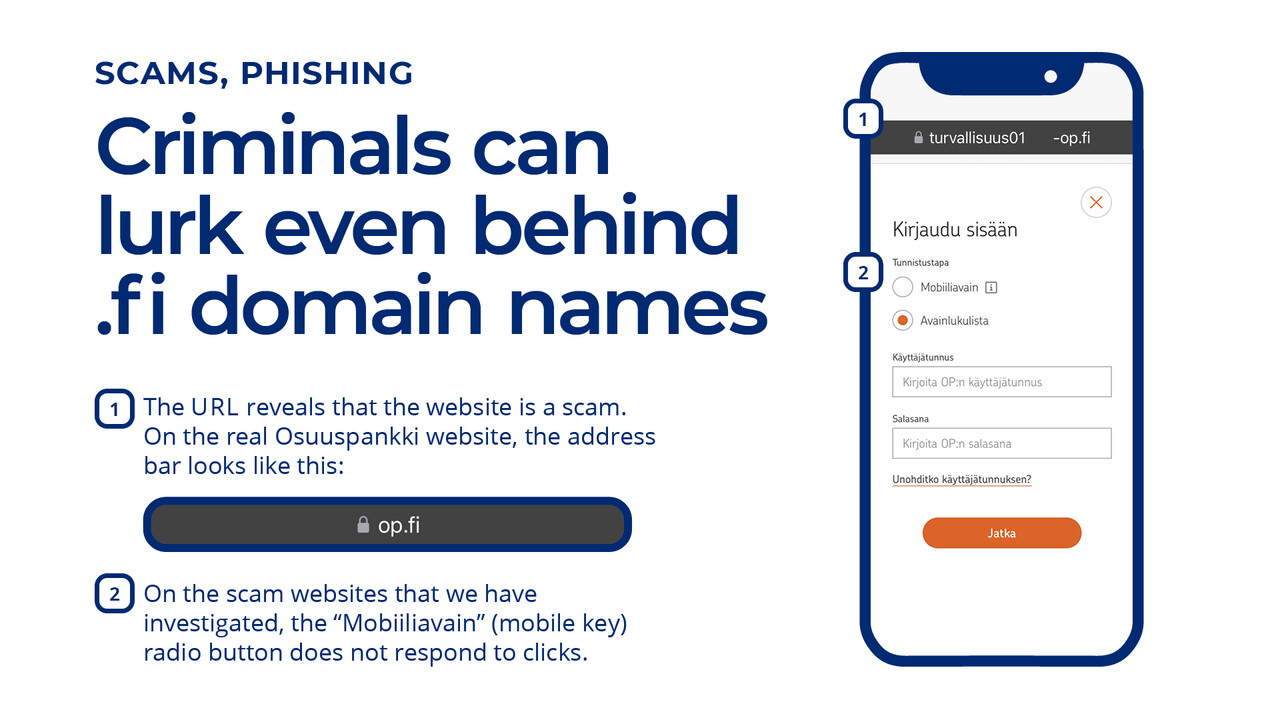
Since the Finnish Transport and Communications Agency Traficom is also responsible for .fi domain names, the NCSC-FI has received numerous requests to take down phishing websites using the .fi domain name extension. Many parties have also asked or suggested that the registration of .fi domain names should be prevented or that the websites should be taken down immediately.
If Traficom has the technical means of ultimately controlling all .fi domain names, why does the agency not immediately shut down all .fi domain names that are being used for malicious purposes or outright prevent their registration? The answer to this question can be found in legislation. As a general rule, the Finnish Transport and Communications Agency cannot monitor (External link) the content of websites or assess whether website content complies with legislation. An exception to this would be if a .fi domain name was involved in a major information security incident that posed a general threat, as in this case access to the domain name could be prevented under certain conditions.
The above does not mean that Traficom and the NCSC-FI do not monitor the registration of malicious domain names and intervene in their operation. On the contrary, the NCSC-FI is constantly monitoring websites that pose a threat to information security and reacts to these threats as quickly as possible when information security incidents are detected.
However, seeing as how domain names play a major role in information exchange and even the realisation of people’s basic rights these days, websites are never taken down lightly. For the same reason, the registration of domain names cannot simply be blocked. Access to a website will only be blocked temporarily and on a case-by-case basis after due consideration if other intervention methods prove ineffective. Even then, the website will first be investigated by the NCSC-FI’s specialists to ensure that it actually poses a major information security risk. Major information security risks include generally accessible websites that phish for bank credentials.
“Bank credentials are a means of strong electronic identification, the hijacking of which can cause a great deal of both monetary and human damage and suffering. In some cases, criminals have managed to withdraw large sums from bank accounts and use strong identification to take out loans or make other commitments,” says Information Security Specialist Olli Hönö from the NCSC-FI. “It is therefore important to pay particular attention to what kind of websites ask for your bank credentials and think twice before entering them.”
Your alarm bells should start ringing if you receive an unexpected notification of a new device having been added to your online bank, for example. The right thing to do in such a situation is to immediately call your bank’s deactivation service phone number. You should also keep in mind that scammers can send fraudulent messages in the name of banks in an attempt to cause alarm and prompt the recipient into rash action.
Multi-factor authentication protects user accounts, but is no substitute for user vigilance
Some of the most common information security problems have to do with user authentication, i.e. user accounts. Every day, the NCSC-FI receives reports of various types of phishing attacks aimed at obtaining usernames and passwords from both organisations and individual citizens. Phishing attacks can be carried out via any channel, but the most common are phishing messages sent via email or text messages.
One effective way to protect your user accounts is to use multi-factor authentication (MFA). That being said, MFA is not enough to prevent data breaches by itself; the user still has to remain vigilant as well.
Some phishing websites are designed to also ask for the one-time authorisation codes used in multi-factor authentication (MFA codes). Because of this, it is important to always check the address of any website that you are about to log in to. Criminals can also use social engineering methods to try and obtain your MFA code or get you to approve a login attempt. Such methods have been seen in Facebook phishing scams, for example. The scammers will ask the victim for their MFA code by claiming that it is related to redeeming a prize draw win, for example. In reality, the code allows the criminal to hijack the victim’s user account.
Another method that criminals use to bypass multi-factor authentication is a so-called MFA fatigue attack. In an MFA fatigue attack, the criminal has already gotten hold of the victim’s username and password and attempts to log in with them multiple times. This causes the victim to be flooded with authentication requests, with the idea being to get the victim to inadvertently approve an authentication request via their authenticator app.
Some widely used services and applications will notify users of any login attempts that are made from abroad or otherwise unusual. If you receive such a notification and do not recognise the login attempt, it is generally a good idea to change your password for the account in question. Organisations should also monitor their users’ logins and take action if they detect unusual login attempts from abroad.
Multi-factor authentication should be enabled whenever possible. However, you should always be cautious of where you enter your MFA code and which authentication request you approve.
For more information on the subject, please see our following publications:
Back to school! Staying safe on the digital school path
The past week marked the start of a new school year in Finland. This year, there are approximately 170,000 pupils studying in primary school grades 1–3 in Finland, many of whom have just received their first phones. As such, the autumn is a good time for parents and children to get together to practice how to use mobile devices at home and in school.
Today, phones are used for much more than just making calls and sending messages. In fact, people’s digital identities and their management are increasingly centred around mobile devices. Because of this, it is a good idea to teach children the right ways of doing things from the get-go, such as taking care of devices (updates), managing personal data (data protection), creating good passwords , password management and multi-factor authentication (information security).
It is a good idea for us adults to refresh our memory from time to time as well. After all, many young schoolchildren today have parents who were part of the first generation to be introduced to the internet in primary and lower secondary school. Unfortunately, the internet has not gotten any safer for children from those times. As such, parents should take an interest in and monitor what their children do on their own phones, what kind of software they use, what kind of content they consume and what they can access on their mobile devices. It is also a good idea to check the age restrictions of applications and especially the privacy settings of applications intended for children.
Learning the ins and outs of today’s digital world requires effective cooperation between children and adults. Having a phone has become a necessity, but parents can still have concerns about their child using one. On the one hand, a child has the right to privacy and secrecy of communications. On the other hand, parents have an obligation to take care of their child’s well-being. Unfortunately, the circumstance under which guardians can read messages on their child’s phone or locate their child’s phone without the child’s permission, for example, are not clearly defined in legislation. As such, the best course of action is to prepare and establish rules for using a phone and communicating online from the get-go.
In our 22/2023 weekly review (External link)in June, we talked about how to take control of devices together with your child.
Vulnerabilities made for rainy Cyber Weather in July
This past week also saw the publication of the Cyber Weather report for July. The month was marked by the publication of several critical vulnerabilities. In relation to these, the NCSC-FI also carried out surveys on vulnerable devices located in Finland. Phishing attacks involving criminals impersonating the suomi.fi service and banks were also frequent in July.
The July Cyber Weather report includes an updated list of the top five threats. Meanwhile, the long-term trends section of the July report takes a look at participation in digital environments.
ABOUT THE WEEKLY REVIEW
This is the weekly review of the National Cyber Security Centre Finland (NCSC-FI) (reporting period 4–10 August 2023). The purpose of the weekly review is to share information about current cyber phenomena. The weekly review is intended for a wide audience, from cyber security specialists to regular citizens.